On November 3rd, the Balancer V2 protocol and its fork projects were attacked across multiple chains, resulting in severe losses exceeding $120M. BlockSec issued an early warning[1] and provided a preliminary analysis conclusion[2]. This was a highly complex attack event. Our initial analysis indicates that the root cause was the attacker manipulating the invariant, distorting the calculation of the BPT (Balancer Pool Token) price, which is the LP token of the Balancer Pool, allowing them to profit from a single batchSwap operation in a stable pool.
Background Knowledge
1. Scaling and Rounding
To unify the decimal places of different tokens, the Balancer contract will:
- upscale: scale the balances and amounts to a unified internal precision for calculations;
- downscale: scale the results back to native precision and perform directional rounding (for example, inputs are usually rounded up to ensure the pool does not under-receive; output paths often have downward truncation).
Conclusion: In the same transaction, the asymmetrical rounding directions used in different stages can create systematic minor deviations when executed repeatedly in very small steps.
2. D and BPT Price
The attack affected the Composable Stable Pool[3] of the Balancer V2 protocol and the forked protocols. The Stable Pool is used for assets expected to maintain a near 1:1 exchange ratio (or for assets exchanged at known rates), allowing for large exchanges without significant price impact, thereby greatly enhancing the capital efficiency between similar or related assets.
- This pool uses Stable Math (based on Curve's StableSwap model), where the invariant D represents the "virtual total value" of the pool.
- The price of BPT (the LP Token of the Pool) is approximately:
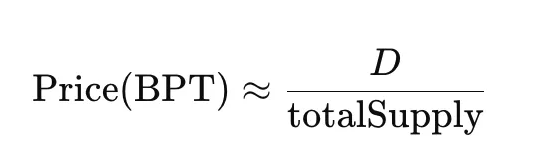
From the above formula, it can be seen that if D can be made to appear smaller on paper (even if the funds have not actually been lost), the BPT price can be made cheaper. BPT represents the share of the Pool, which is used to calculate how much Reserve can be obtained when withdrawing liquidity. Therefore, if the attacker can acquire more BPT, they can profit when withdrawing liquidity.
Attack Analysis
Taking an attack transaction on Arbitrum as an example, the batchSwap operation can be divided into three stages:
First Stage: The attacker exchanges BPT for underlying assets, precisely adjusting the balance of one of the tokens (cbETH) to the critical point of the rounding boundary (amount = 9). This step creates conditions for the precision loss in the next stage.
Second Stage: The attacker uses a carefully constructed amount (= 8) to swap between another underlying asset (wstETH) and cbETH. Due to rounding down when scaling the token amounts, the calculated Δx is slightly smaller (from 8.918 to 8), leading to an underestimation of Δy and causing the invariant D (from Curve's StableSwap model) to decrease. Since BPT price = D / totalSupply, the BPT price is artificially suppressed.
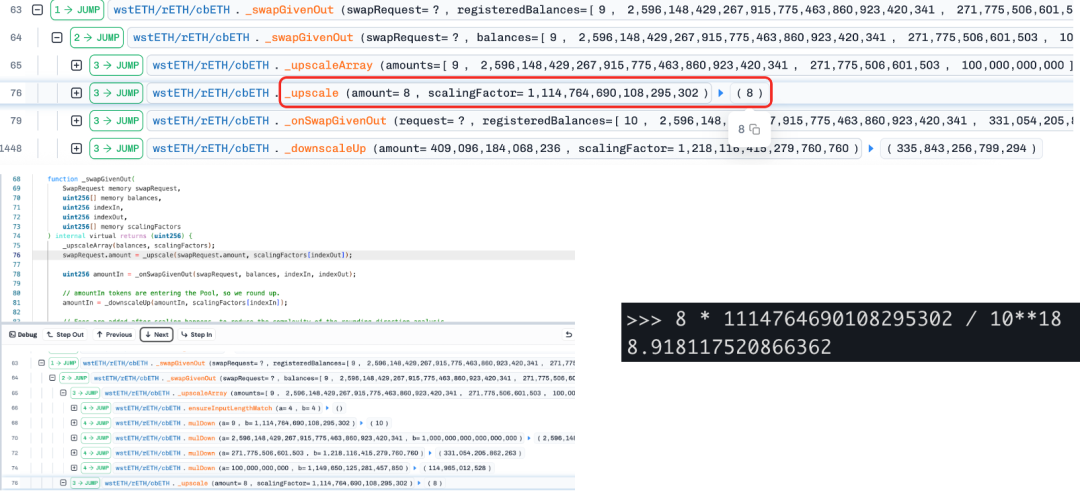
Third Stage: The attacker reverses the exchange of underlying assets back to BPT, restoring balance in the pool while profiting from the suppressed BPT price -- acquiring more BPT Tokens.
Finally, the attacker uses another profitable transaction to withdraw liquidity, thereby profiting from the additional BPT obtained to acquire other underlying assets (cbETH and wstETH) from the Pool.
Attack Transaction:
https://app.blocksec.com/explorer/tx/arbitrum/0x7da32ebc615d0f29a24cacf9d18254bea3a2c730084c690ee40238b1d8b55773
Profitable Transaction:
https://app.blocksec.com/explorer/tx/arbitrum/0x4e5be713d986bcf4afb2ba7362525622acf9c95310bd77cd5911e7ef12d871a9
Reference:
[1]https://x.com/Phalcon_xyz/status/1985262010347696312
[2]https://x.com/Phalcon_xyz/status/1985302779263643915
[3]https://docs-v2.balancer.fi/concepts/pools/composable-stable.html
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




