Author: Louis, Trendverse Lab
In early November 2025, the decentralized finance (DeFi) sector was once again shaken by a sudden event.
The established protocol Balancer suffered a severe security vulnerability within just a few hours, with approximately $128 million in assets being transferred out of its core vault, involving mainstream tokens such as ETH, wstETH, and osETH.
Unlike traditional reentrancy attacks, this incident was not a simple exploitation of a contract vulnerability but a precise infiltration targeting Balancer's core architecture. The attacker exploited a logical flaw in the protocol's access control, opening a gap in the Vault layer, which is considered the cornerstone of the system.
This design, once praised by the industry for being "efficient, elegant, and modular," ultimately backfired as a single point of weakness in the system. From a technical perspective, this was a collapse of the "trust boundary"; from an industry perspective, it revealed the long-term tension between the complexity of DeFi protocols and security governance. To understand the root of this crisis, we must return to its starting point—the Balancer itself, which was once regarded as a model of DeFi architecture.
1. The Trusted Veteran
Balancer is a decentralized exchange (DEX) protocol built on Ethereum and is one of the most representative automated market makers (AMMs) in the cryptocurrency space.
Since its launch in 2020, it has provided a new paradigm for traditional AMMs like Uniswap with its innovative mechanism of "multi-asset pools + automated rebalancing": users can not only configure multiple assets in a single liquidity pool but also customize weight and fee structures, allowing for more flexible liquidity management.
Thanks to this highly customizable design, Balancer once became one of the most mature protocols in the DeFi ecosystem, with its total value locked (TVL) reaching hundreds of millions of dollars at one point.
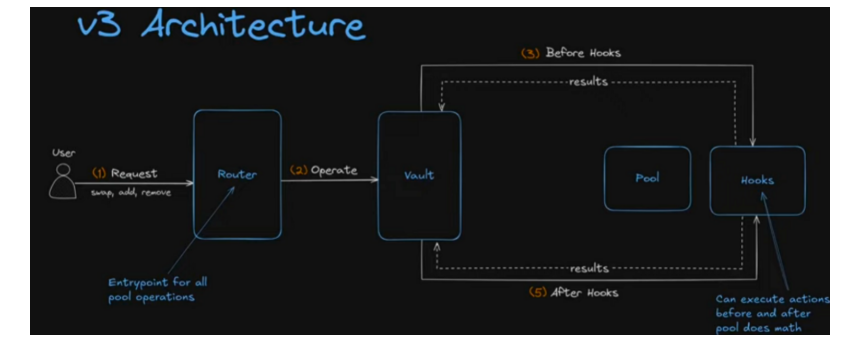
Image Source: Balancer Official Web
In the latest upgrade of the Balancer V3 architecture, the protocol further evolved from "fund management" to "smart fund orchestration."
Every user operation (whether swapping, adding liquidity, or withdrawing) goes through a clear instruction path: the instruction is first received and routed by the Router, then the Vault uniformly schedules the funds. The Vault triggers Hooks—pluggable logic modules used to perform additional checks or calculations before and after transactions.
The entire system is built around the core process of "Router takes orders, Vault manages funds, Pool executes, Hooks extend," creating a modular and programmable trading infrastructure.
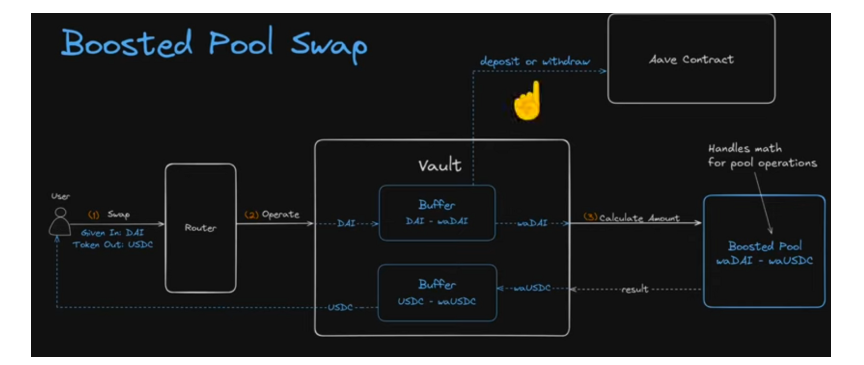
Image Source: Balancer Official Web
On this basis, Balancer also introduced the Boosted Pool mechanism, further enhancing capital utilization efficiency.
When users perform a swap (e.g., DAI → USDC), the Vault not only directly handles the user's original tokens but also automatically interacts with external protocols (like Aave) to deposit and withdraw corresponding wrapped tokens (like waDAI, waUSDC), achieving dual utilization of liquidity and yield. When the pool's funds are insufficient, the Vault automatically redeems; when there are idle funds, it automatically deposits them into external protocols to earn interest. This allows for a dynamic balance between "available liquidity" and "yield optimization." However, like V2, it is precisely this centralized fund scheduling logic that has sown the seeds of systemic risk. As the central hub of all fund flows, any vulnerability in the Vault not only affects a single pool but could impact the entire protocol and even the cross-chain ecosystem. The Boosted Pool further expanded the Vault's responsibilities, making it not only responsible for internal fund settlement but also for interacting with external protocols, which means the risk of attack has extended from a single protocol to a multi-protocol level. Although V3 has significantly improved module isolation and permission control in its architecture, the target of this attack was not the new version itself but the still-active V2 instances on-chain. (The vulnerability was confirmed by multiple security agencies, including PeckShield and SlowMist, in on-chain transaction tracing, and the official announcement also confirmed that the issue occurred in the V2 contract.)
In the following sections, we will review the process of this attack and further explore—under the premise that V3 has already been launched, why has V2 not been retired? The risk management logic reflected in this decision reveals the long-standing contradiction between technological evolution and asset security in DeFi protocols.
2. Vault: The Cost of Security "Illusion"
Since its launch in 2020, Balancer has experienced multiple security incidents—from the early deflationary token vulnerability to the V2 pool precision issues in 2023, and the Velocore fork attack in 2024. Each vulnerability exposed systemic risks in different forms, but the team has always managed to regain user trust through rapid upgrades, parameter fixes, and community communication.
However, the attack in 2025 was different from previous ones: this time, the problem lay in the security design at the core logic layer of the protocol, rather than traditional front-end or external call issues.
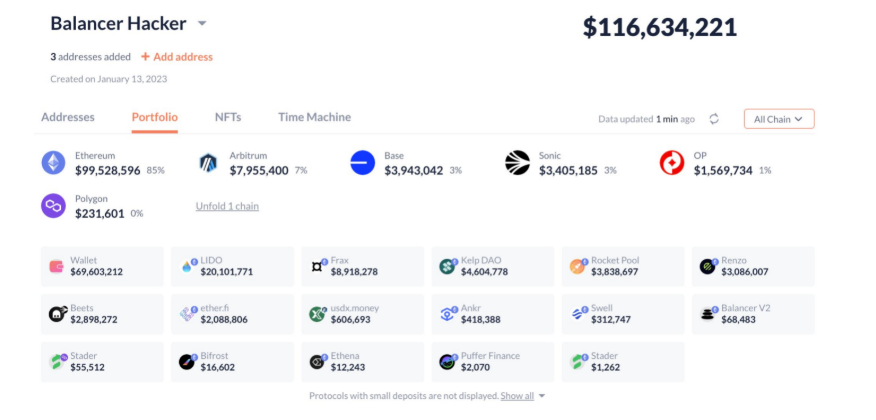
Image Source: TwitterLookonchain (This image is easy for readers to see the distribution ratio; the total loss figure is mentioned below)
As of November 3, multiple security agencies and media estimated that the total loss caused by the attack was approximately $128 million, involving assets across multiple chains (including Ethereum, Base, Berachain, etc.).
Setting aside the complex code side, unlike traditional reentrancy attacks or front-end phishing, the root of this incident lies in the flaw in the internal permission logic of the V2 Vault. The attacker did not destroy the system architecture but instead disguised themselves as an internal account of the protocol through legitimate interfaces, successfully triggering a withdrawal function intended for internal use only. As a result, the system misjudged their identity, treating the large funds as authorized withdrawals and transferring out high liquidity assets such as Ethereum-based and liquid-staking tokens in one go.
In other words, "the Vault misidentified the attacker as one of its own" is not merely a coding error but a more subtle design imbalance—when the protocol pursues higher generality and modularity, security isolation is often sacrificed. Even after multiple rounds of audits, such vulnerabilities in the "logical layer trust assumption" may still be overlooked. It reveals a key reality: DeFi security risks have long evolved from single-point code reviews to systemic issues of architectural design and permission boundaries.
So why did the attacker target V2 only?
The reason is that the V2 Vault is still active on-chain and holds a large amount of un-migrated funds and ecosystem assets.
Some DAO liquidity pools, yield aggregators, and early liquidity protocols still rely on V2 contracts, making comprehensive migration face high costs in terms of technology, governance, and consensus.
The attacker exploited this reality, targeting the access control vulnerability in the internal balance management function of V2. In contrast, V3 has restructured this logic, introducing a layered mechanism with Router and Hooks, decoupling permissions and operation paths to avoid similar risks. A deeper hidden danger lies in governance decisions. The Balancer team did not immediately retire V2 after launching V3, partly due to considerations of compatibility and ecological cooperation, choosing to allow both generations of architecture to operate in parallel.
This "coexistence of old and new" transitional strategy is commercially reasonable but creates a gray area in terms of security:
The design vulnerabilities of the old version and the open interfaces of the new system coexist, and once exploited, localized risks can quickly spread into systemic events across protocols and assets.
3. The Chain Reaction Beyond the Vulnerability
The true impact of this attack extends far beyond the financial level. The event triggered a chain reaction across ecological, market, and psychological dimensions, exposing the fragile connections and trust gaps within the DeFi system.
1. Ecological Level: The Infectious Risk of Open Source Reuse
Balancer's open-source code has been widely reused and forked, becoming the foundational module for many AMM projects and on-chain components. This means that the vulnerability of a single protocol is no longer confined to itself but can quickly spread throughout the entire ecosystem.
When the V2 Vault or pool was exploited, fork projects and integrators using the same logic were forced to take emergency measures. For example, Berachain temporarily paused network operations and conducted emergency repairs to prevent the attack path from spilling over.
This "code-level contagion" expands the trust boundary of DeFi from a single protocol to the entire system ecosystem:
A single vulnerability not only undermines the security of one application but also shakes the stability of the entire on-chain capital network.
2. Market Level: Instant Feedback of Funds and Prices
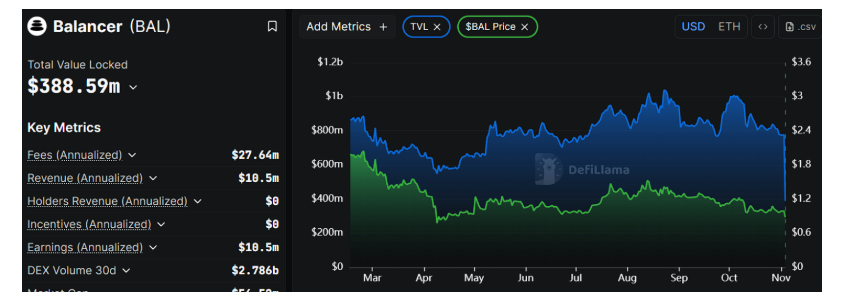
Data Source: Defilama
The market's response to risk is extremely rapid.
According to DeFiLlama data, as of November 3, 2025, Balancer's total value locked (TVL) plummeted from approximately $775 million to $392 million, a nearly 50% drop within 24 hours.
Correspondingly, several fork protocols based on Balancer's code also experienced over 30% TVL retracement during the same period. Deployments on some affected chains were forced to pause or go offline to prevent further risk transmission.
These data indicate that in a decentralized ecosystem, capital migration and price adjustments occur almost simultaneously, and the speed of trust loss is equivalent to the speed of capital flow.
3. Psychological Level: The Fragility of Audit Endorsements and Trust Repricing
This incident once again shook the market's confidence in the traditional trust mechanism of "security audits."
Even after multiple rounds of scrutiny by top auditing firms, protocols can still fail due to ambiguous logical boundaries or historical technical debts.
It has been proven that audit results cannot replace long-term structural security guarantees. For LPs (liquidity providers) and ordinary users, the impact of this incident is not just short-term price losses but an increase in trust costs.
They began to reassess the value of "security" as an intangible asset, leaning towards divesting or diversifying their allocations, thereby amplifying market volatility.
4. The Position and Future of DeFi: The Restructuring of Trust and the Reality Check
The Balancer incident once again confronts the crypto industry with the question that has been repeatedly raised yet remains unavoidable:
——Is DeFi really "decentralized"?
The attack exposed not just isolated technical vulnerabilities but the structural contradictions of the entire decentralized finance system:
The tension between ideals and reality.
The original intention of DeFi is to "remove the center and reconstruct trust," but as the ecosystem expands and system complexity increases, its security dependencies have begun to re-centralize—from auditing agencies, oracle networks, contract templates, to cross-chain bridges and custodial layers. Each "decentralized" component has gradually formed new centers in its operational logic.
The Balancer Vault hacking incident is a microcosm of this trend.
It represents the industry's ongoing pursuit of efficiency and integration—centralized fund management, improved capital utilization, and reduced friction costs. However, when efficiency outweighs security, and composability takes precedence over isolation, the boundaries of "decentralization" quietly blur.
The so-called open finance is evolving into a more complex structure with greater central dependencies.
From a longer-term perspective, this incident will not lead to a retreat of DeFi; rather, it may become a watershed moment for the industry to enter the next stage.
The future of DeFi will no longer be limited to "automated market making" or "yield aggregation," but will evolve into a "verifiable financial system":
Contract logic must be continuously monitored and verified, AI agents and on-chain security layers will jointly bear risk defense, and every change in governance and fund scheduling can be verified in real-time rather than retrospectively.
In other words, the next stage of DeFi is not "more decentralized," but rather more transparent, more traceable, and more verifiable.
Trust remains core; it is just that its expression is changing: from "trusting the code by default" to "ensuring the code is continuously verified."
Perhaps the losses of Balancer serve as a costly lesson.
It reminds all builders and investors—
Decentralization is not the end, but a continuous process.
Every upgrade, every migration, every audit is validating whether this experiment in trust is sustainable enough.
From the perspectives of investment and governance, this also means that risk pricing is no longer just a market behavior but a collaborative result between code logic and consensus mechanisms.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




