Original Title: "Analysis of the $26.44 Million Contract Vulnerability in Truebit Protocol Theft"
Original Source: ExVul Security
On January 8, 2026, the Truebit Protocol was attacked by hackers, resulting in a loss of 8,535.36 ETH (approximately $26.44 million). The Truebit Protocol team confirmed the incident early the next morning. The ExVul security team conducted a detailed vulnerability analysis of this attack, with the following results:
Attack Process
Attacker Address:
0x6c8ec8f14be7c01672d31cfa5f2cefeab2562b50
Attack Transaction Hash:
0xcd4755645595094a8ab984d0db7e3b4aabde72a5c87c4f176a030629c47fb014
The attacker completed the attack by looping through 4 rounds of calling getPurchasePrice→0xa0296215→0xc471b10b, analyzing the first loop as an example.
- The attacker first calls the getPurchasePrice(240442509453545333947284131) function, which returns 0.
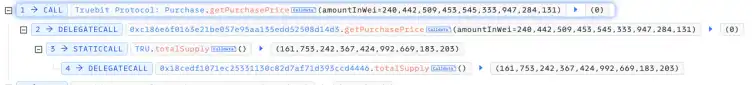
- The attacker calls the 0xa0296215(c6e3ae8e2cbab1298abaa3) function, with msg.value set to 0. Ultimately, 240442509453545333947284131 TRU tokens are successfully minted.
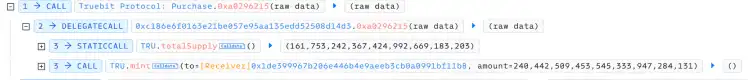
- The attacker calls the 0xc471b10b(c6e3ae8e2cbab1298abaa3) function. Ultimately, 240442509453545333947284131 TRU tokens are destroyed, resulting in the acquisition of 5105.06 ETH.
Attack Logic Analysis
By understanding the above attack process, it is evident that there is a logical issue with the getPurchasePrice function and the 0xa0296215 function. Below is a deeper analysis (since the contract is not open source, the following code is all decompiled code).
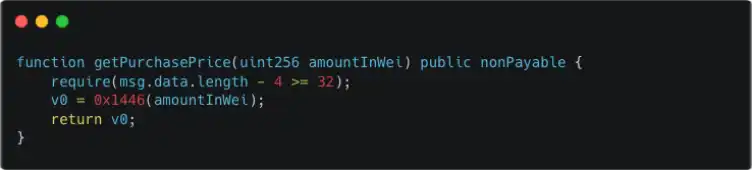
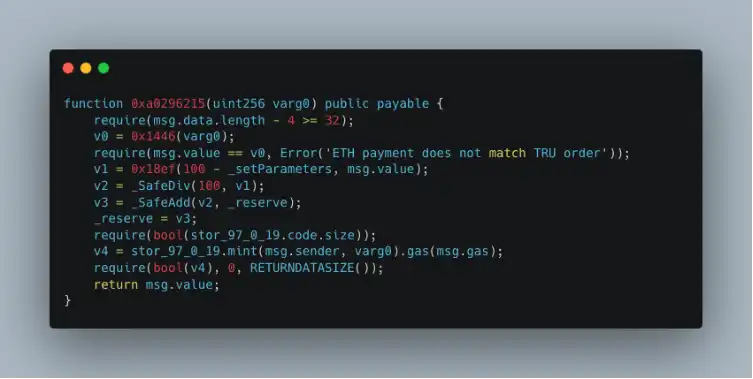
By comparing the common points of the two functions, we can find that the 0x1446 function is used to determine how much ETH is needed to purchase a specified amount of TRU. Clearly, there is a problem with the logic of the 0x1446 function, leading to incorrect ETH calculations. Below is a detailed analysis of the logic in the 0x1446 function.
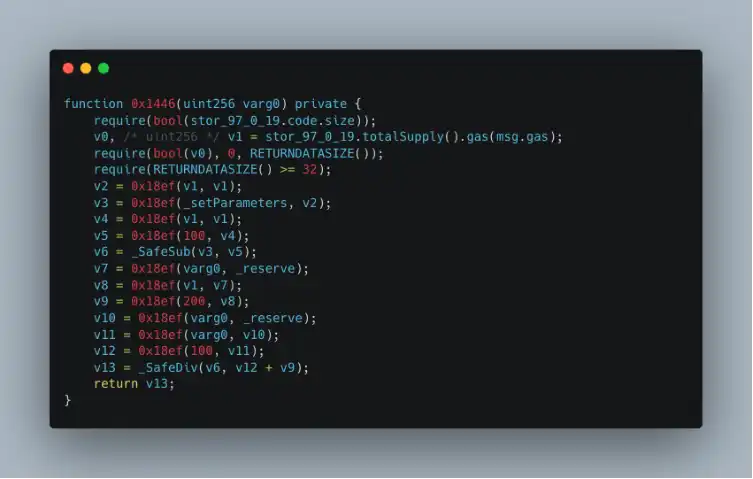
Observing the logic in the 0x1446 function, since the final calculation result v13 == 0, there must be an issue with the calculation logic mentioned above. It is important to understand that the 0x18ef function is the same as _SafeMul, so the problem lies in using the native addition v12 + v9 (the contract version is ^0.6.10, so there is no overflow check).
v12 and v9 represent:
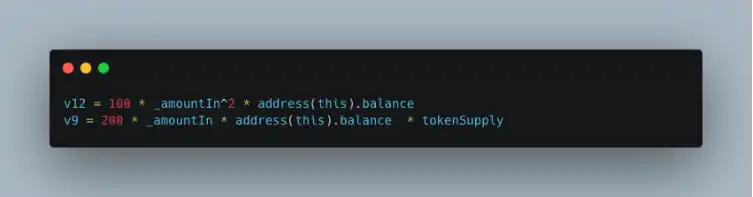
From the above analysis, the attacker's strategy is to input a large _amountIn, causing v12 + v9 to overflow into a very small value, ultimately making (v12 + v9) / v6 == 0.
Conclusion
The fundamental reason for the attack on Truebit Protocol lies in the serious integer overflow vulnerability in its token purchase price calculation logic. Since the contract uses Solidity version ^0.6.10 and does not perform safety checks on critical arithmetic operations, it ultimately resulted in a significant loss of 8,535.36 ETH. The newer versions of Solidity have already mitigated overflow vulnerabilities. This attack appears to be hackers utilizing AI to automatically scan for vulnerabilities in older DeFi protocols that are already online (including recent attacks on Balancer and yETH). We believe that such AI-driven attacks on older DeFi protocols will become increasingly common, so we recommend that project teams conduct new security audits of their contract code. If vulnerabilities are found, they should promptly upgrade the contract or transfer assets, and ensure on-chain monitoring to detect anomalies in a timely manner, minimizing losses.
This article is from a submission and does not represent the views of BlockBeats.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




