On November 19, 2025, the U.S. Department of the Treasury's Office of Foreign Assets Control (OFAC) officially added former Canadian Olympic snowboarder Ryan James Wedding and his core associates and entities to the sanctions list, freezing all of their assets within the United States and prohibiting U.S. citizens from engaging in any transactions with the related parties. Following this, the U.S. State Department raised the reward amount to $15 million, and the Mexican Embassy in China simultaneously released a reporting tutorial. The FBI, Royal Canadian Mounted Police, and Mexican police initiated a transnational joint manhunt—this global operation targeting the "Olympic athlete drug lord" unveiled the deep connections between cryptocurrency, transnational drug trafficking, and serial murders. BlockSec, relying on on-chain tracking technology and specialized research data, restored Wedding's trajectory from sports star to crime lord, as well as the complete logic of how he utilized blockchain to construct an "untraceable" criminal funding network.
I. From Olympic Athlete to "World's Most Wanted Criminal"

Born in 1976 in Thunder Bay, Ontario, Canada, Wedding was once a promising star in winter sports. With his aggressive riding style and stable competitive performance, he successfully made the Canadian national team and represented the country at the 2002 Salt Lake City Winter Olympics, where he made a name for himself in the men's parallel giant slalom event. At that time, he was one of the representatives of Canadian winter sports, and the attention both on and off the field made him accustomed to the spotlight, but it also planted the seeds of an obsessive desire for "quick success."
After the Olympics, Wedding's life trajectory took a sharp downturn. He rejected a contract renewal offer from a professional team, abandoned his long-cultivated skiing career, and turned to the high-risk business sector, ultimately intersecting with a transnational drug trafficking organization. In 2008, he was arrested in California for cocaine smuggling and was sentenced to four years in prison in 2010—this prison experience not only did not lead him to repent but instead became a "springboard" for expanding his criminal network, as the various criminals he met in prison laid the foundation for his future transnational drug trafficking network. After his release, Wedding completely tore off the disguise of a "former Olympic athlete," transforming into the crime lord codenamed "El Jefe" (Spanish for "the Boss"), establishing a drug trafficking organization named after himself (Ryan Wedding Drug Trafficking Organization), which was recognized by U.S. and Canadian authorities as an "independent criminal entity."
Wedding's criminal group is known for its bloody violence and precise operations. By deeply colluding with the Sinaloa drug cartel in Mexico (designated as a "terrorist organization" by the U.S. in 2024), they constructed a smuggling route from Colombia's cocaine production areas, through Mexico, and ultimately to the U.S. and Canada, trafficking up to 60 tons of drugs annually, with an annual involvement amount exceeding $1 billion, becoming one of the main threats to Canadian national security. To maintain the criminal network, Wedding did not hesitate to resort to murder: in November 2023, after a batch of drugs was stolen, he ordered a massacre in Ontario, Canada, resulting in 2 deaths and 1 serious injury; from April to May 2024, his gang carried out two consecutive murders, with victims including associates who owed drug debts; in January 2025, to cover up his crimes, he instructed his subordinates to execute federal witness Acebedo Garcia at close range in a restaurant in Colombia, with the victim shot five times in the head and dying on the spot, while Wedding's lawyer participated in the planning, even suggesting "dealing with the witness to withdraw the charges."
In March 2025, Wedding officially made it onto the FBI's Ten Most Wanted Fugitives list, replacing the previously wanted Alexis Flores, and Interpol simultaneously issued a red notice. He is now hiding in Mexico, sheltered by a core member of the local drug cartel, "El General" (Édgar Aarón Vázquez Alvarado), remotely controlling the criminal network through encrypted communication tools, while his associated Mexican entities such as VRG Energéticos and Grupo RVG Combustibles serve as a "legitimate cover" for concealing criminal activities.
II. Money Laundering Process
According to the indictment, Wedding's criminal group primarily launders drug trafficking proceeds in the form of U.S. dollars, Canadian dollars, and cryptocurrencies. Among them, for cryptocurrency assets, the criminal group splits large amounts of money into multiple small transfers, quickly completing the transfer through intermediary USDT wallets, and ultimately consolidating the funds into a central Tether wallet controlled by the defendant WEDDING.
The main individuals responsible for the money laundering work are SOKOLOVSKI, HOSSAIN, and CANASTILLO-MADRID, along with other known or unknown individuals identified by the grand jury, who are referred to as members of the "Wedding Criminal Organization."

Money Laundering Operations of Drug Proceeds
d. Wedding's criminal gang conceals its massive profits from cocaine sales in the U.S. and Canada within U.S. dollars and cryptocurrencies.
e. Regarding the use of cryptocurrencies: to obscure the original source of the funds, members and associates of Wedding's criminal gang utilize a complex Tether (USDT) network to implement the following operations: (1) splitting large amounts of money into multiple small transfers; (2) quickly transferring funds through intermediary USDT wallets, ultimately consolidating to the core Tether wallet controlled by the defendant Wedding.
f. Defendants Sokolovski, Hossain, Canastillo-Madrid, and other known and unknown individuals of the grand jury provide services to members of Wedding's criminal gang (i.e., defendants Wedding and Clark)—specifically including concealing their drug trafficking proceeds and using these proceeds to promote and facilitate the gang's criminal objectives. The following diagram illustrates a simplified flowchart of this money laundering system.
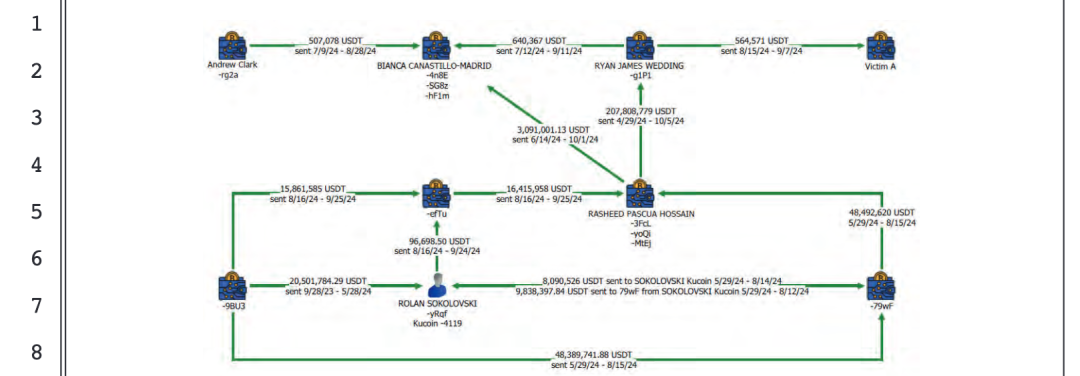
The following is a detailed description of the money laundering process.

Money Laundering Operations of Drug Proceeds
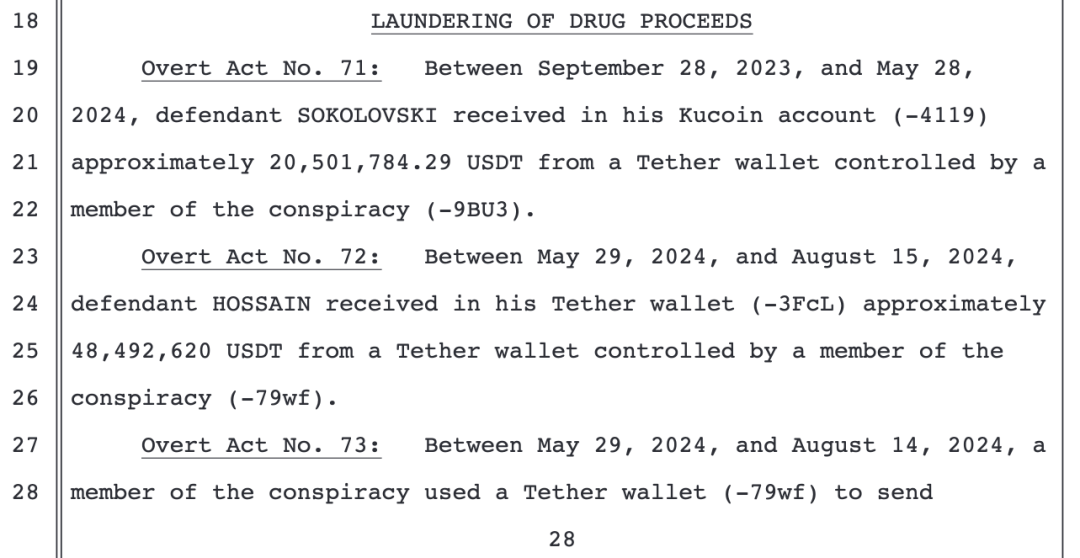
Item 71: From September 28, 2023, to May 28, 2024, defendant Sokolovski received approximately 20,501,784.29 USDT transferred from a Tether wallet controlled by a member of the criminal gang into his Kucoin account (-4119).
Item 72: From May 29, 2024, to August 15, 2024, defendant Hossain received approximately 48,492,620 USDT transferred from a Tether wallet controlled by a member of the criminal gang into his Tether wallet (-3FcL).
Item 73: From May 29, 2024, to August 14, 2024, a member of the criminal gang transferred approximately 8,090,526 USDT from a Tether wallet (-79wf) to defendant Sokolovski's Kucoin account (-4119).
Item 74: From May 29, 2024, to August 12, 2024, defendant Sokolovski transferred approximately 9,838,397.84 USDT from his Kucoin account (-4119) to a Tether wallet controlled by a member of the criminal gang (-79wf).
Item 75: From June 14, 2024, to October 1, 2024, defendant Hossain transferred approximately 3,091,001.13 USDT from his Tether wallets (-yoQi, -MtEj) to a TRON wallet (-4n8E) controlled by defendant Canastillo-Madrid.
Item 76: From April 29, 2024, to October 8, 2024, defendant Hossain transferred approximately 98.86% of his total funds (approximately 207,808,779 USDT) into defendant Wedding's Tether wallet (-g1P1) through a Tether wallet (-yoQi).
Item 77: On June 18, 2024, Bonilla transferred approximately 17,300 USDT to defendant Hossain's Tether wallet (-yoQi) to settle his drug debt owed to defendants Wedding and Clark.
Item 78: From July 9, 2024, to November 5, 2024, defendant Canastillo-Madrid received approximately 507,078 USDT transferred from a Tether wallet controlled by Clark into his two TRON wallets (-4n8E, -SG8z).
Item 79: From July 12, 2024, to September 11, 2024, defendant Canastillo-Madrid received approximately 640,367 USDT transferred from defendant Wedding's Tether wallet (-g1P1) into his two TRON wallets (-4n8E, -SG8z).
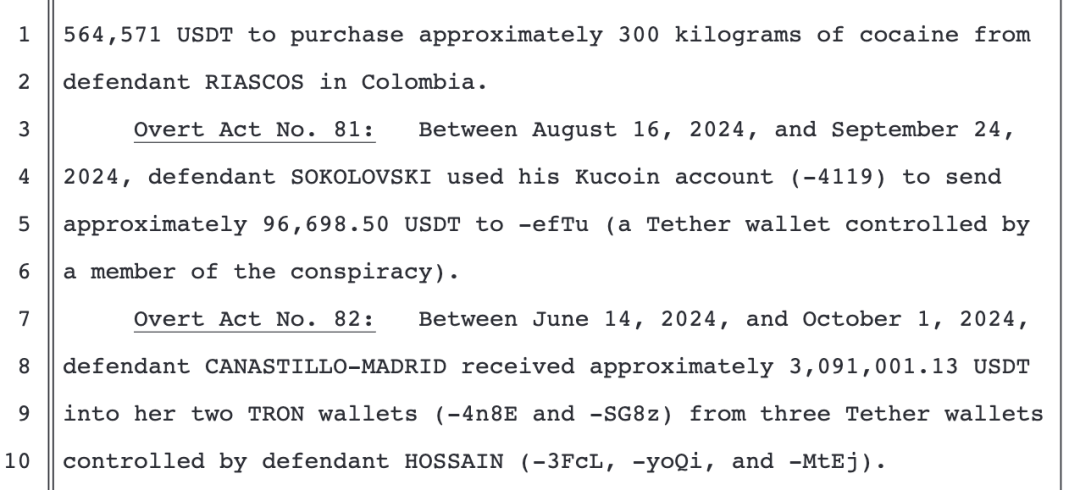
Item 80: From August 15, 2024, to September 7, 2024, defendant Wedding provided approximately 564,571 USDT to victim A, who acted as an intermediary, for the purchase of approximately 300 kilograms of cocaine from defendant Riascos in Colombia.
Item 81: From August 16, 2024, to September 24, 2024, defendant Sokolovski transferred approximately 96,698.50 USDT from his Kucoin account (-4119) to a Tether wallet controlled by a member of the criminal gang (-efTu).
Item 82: From June 14, 2024, to October 1, 2024, defendant Canastillo-Madrid received approximately 3,091,001.13 USDT transferred from three Tether wallets controlled by defendant Hossain (-3FcL, -yoQi, -MtEj) into his two TRON wallets (-4n8E, -SG8z).
We visualize the above money laundering operations in the following diagram.

To further understand the sources and destinations of these funds, we obtained the direct inflows and outflows (greater than $100,000) for these addresses and created the following relationship diagram.
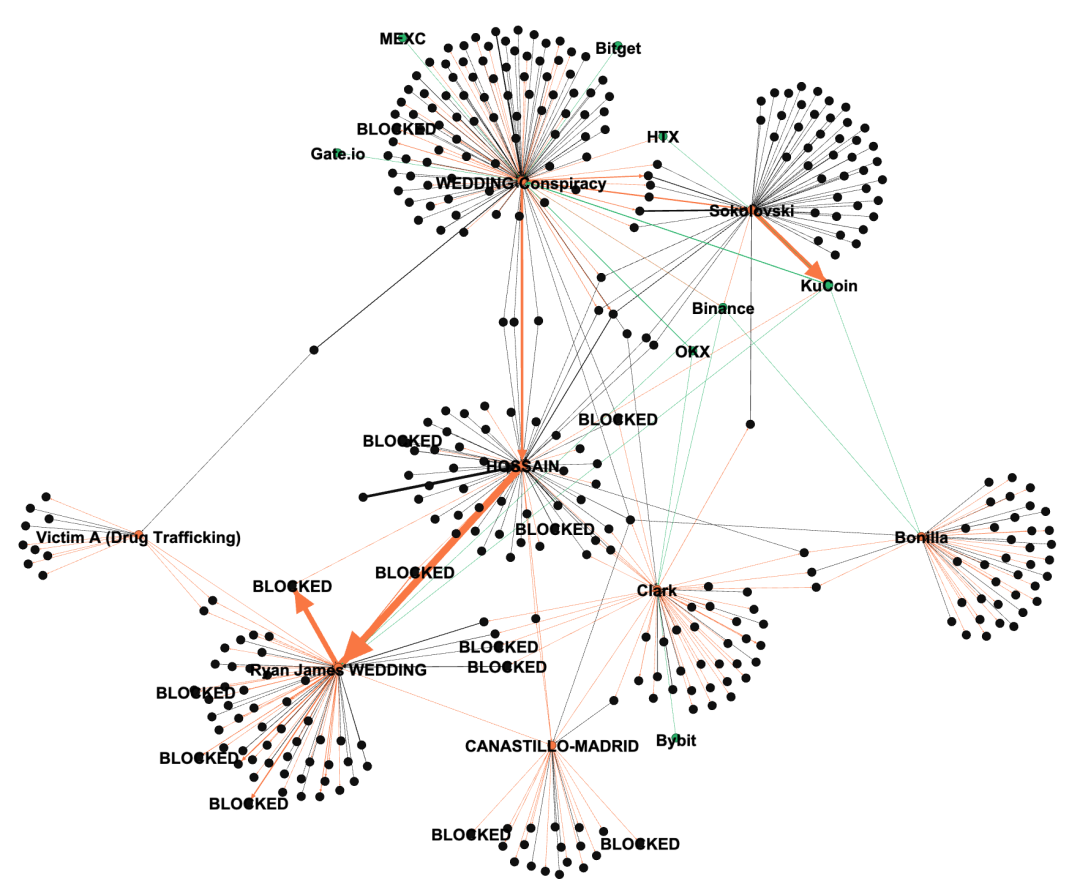
The edges in the diagram represent the flow of funds, with colors consistent with the funds source, and the thickness of the edges correlating positively with the amount of funds.
Key Financial Nodes and Role Distribution
From the fund flow relationship diagram, it can be observed that HOSSAIN and SOKOLOVSKI form two significant financial aggregation centers, while the address cluster labeled "WEDDING Conspiracy" serves as the primary source of funds for these two centers.
This structure indicates that the WEDDING Conspiracy address cluster may undertake upstream functions related to money laundering and drug transactions, continuously supplying downstream nodes with funds that have undergone preliminary obfuscation.
In terms of fund flow, two distinct paths are evident:
- Funds aggregated to SOKOLOVSKI predominantly flow into KuCoin, indicating its primary role in completing final laundering and monetization through centralized exchanges;
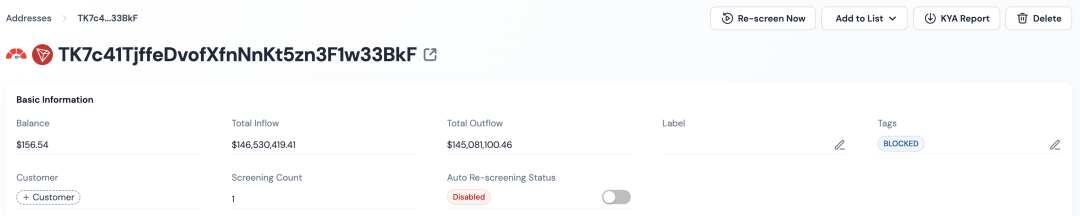
- Funds aggregated to HOSSAIN mainly flow to addresses controlled by Ryan James Wedding, which are then further transferred to an address currently blocked by USDT, TK7c41TjffeDvofXfnNnKt5zn3F1w33BkF (SUSPECT-33BkF).
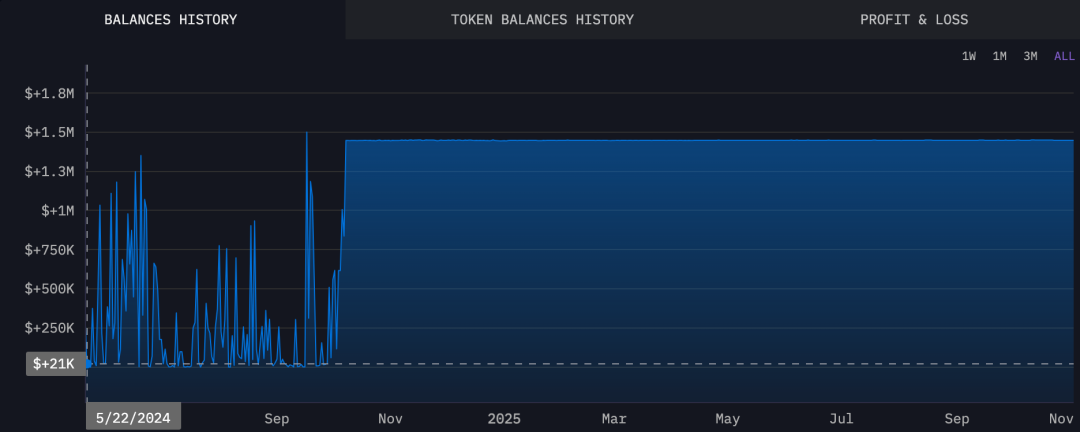
Active time of SUSPECT-33BkF
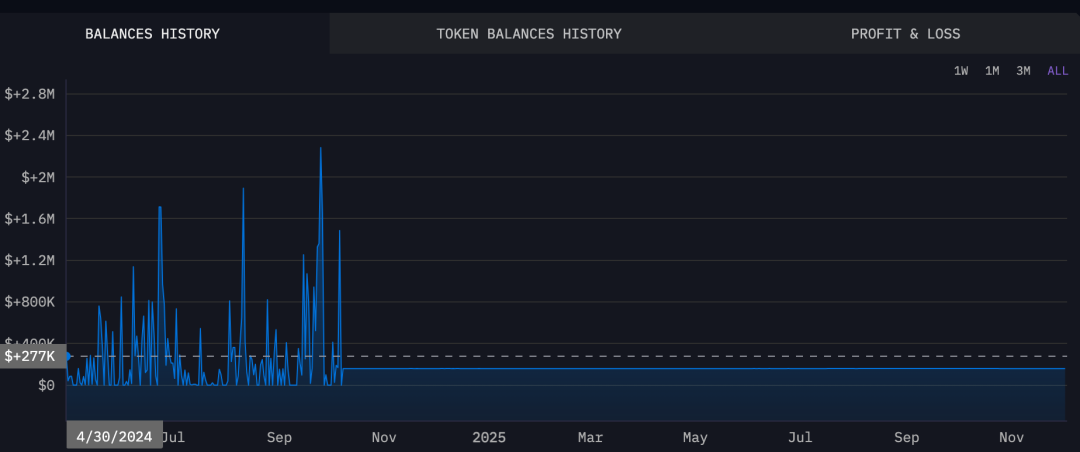
Active time of WEDDING-Yg1P1
Analysis of on-chain activity time shows that SUSPECT-33BkF and WEDDING-g1P1 have highly overlapping active periods, with their time distributions nearly identical. Based on this characteristic, it can be reasonably inferred that SUSPECT-33BkF is an alternative or extended address used by Wedding for continued money laundering activities in subsequent stages.
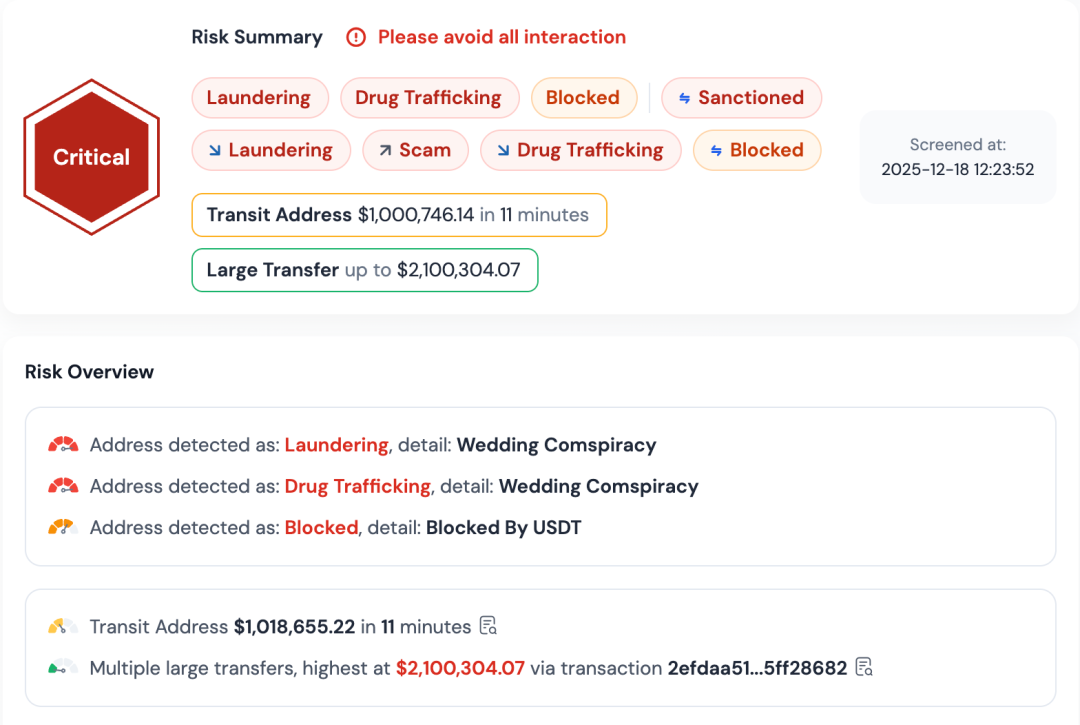
Further analysis of SUSPECT-33BkF using the BlockSecCompliance platform revealed:
- 99.22% of its inflows come from addresses that have been sanctioned or marked (i.e., addresses related to Wedding in this case);
- Nearly 40% of its outflows are directed towards addresses currently blocked by USDT.
This address exhibits a high concentration of both sources and destinations in high-risk entities, further reinforcing its critical position in the money laundering chain of the Wedding criminal organization.
More analysis content:
https://app.blocksec.com/phalcon/v2/address/scan/-2/TK7c41TjffeDvofXfnNnKt5zn3F1w33BkF
III. Industry Insights: Crime Defense and Governance in the Era of Cryptocurrency
The Wedding group case is not an isolated incident. BlockSec's specialized research has found that since 2024, global cross-border crime cases involving privacy coins have increased by 187% year-on-year, with criminal organizations abusing encryption technology showing trends of "professionalization, scaling, and globalization." This case not only exposes the weak links in cryptocurrency asset regulation but also provides important governance insights for the blockchain security industry and law enforcement agencies.
For ordinary users, it is essential to be wary of the misconception that "anonymous transactions = absolute security." The Wedding group case proves that even with privacy coins, transaction trails can still be traced under professional technical analysis, and ordinary users who inadvertently interact with criminally associated addresses may face asset freezing risks. It is recommended to prioritize trading on compliant exchanges, avoid using platforms without KYC certification, regularly check the risk status of wallet-associated addresses using blockchain security tools, and refuse large transfer requests from unknown addresses.
For law enforcement agencies and the industry, it is crucial to establish a collaborative mechanism of "technical tracking + cross-border cooperation + compliance regulation." BlockSec's practice shows that blockchain technology itself is an important tool for combating crime—through address clustering, cross-chain tracking, and behavioral profiling, it can effectively break the "anonymous disguise" of crypto crime. In the future, it is necessary to further strengthen cross-border judicial cooperation, establish a globally unified platform for sharing clues about cryptocurrency crimes, and promote exchanges to implement "KYC + transaction monitoring" obligations, intercepting transactions involving sanctioned lists and high-risk addresses in real-time to curb the flow of criminal funds at the source.
From the glorious moments on the Olympic stage to being a "tainted figure" on the OFAC sanctions list, Wedding's fall from grace is lamentable. His story warns us that the neutrality of technology needs to be correctly guided, and the innovative value of cryptocurrency should not be abused by criminal organizations. BlockSec will continue to delve into blockchain security technology, building a more comprehensive crime tracking model through specialized research, strengthening asset protection for ordinary users, and providing precise and efficient technical support for law enforcement agencies, promoting the cryptocurrency ecosystem towards a direction of "security, compliance, and trustworthiness," ensuring that every cryptocurrency transaction can withstand the scrutiny of sunlight.
Currently, Ryan James Wedding remains hidden in Mexico, and the U.S. State Department has raised the reward amount to $15 million (including $10 million from the drug enforcement reward program + $500,000 from the FBI's special reward), while the Mexican Embassy in China has also launched a multilingual reporting tutorial. Any individual or organization providing effective clues (including his specific hiding address, communication methods, and associated personnel information) and assisting in the arrest of Wedding can submit information and claim the reward through the following channels:
- FBI official channel: Submit anonymous tips by logging into the FBI website's "Ten Most Wanted Fugitives" section (www.fbi.gov/wanted/topten);
- Mexican law enforcement: Submit information through the encrypted reporting platform of the Mexican Attorney General's Office (FGR);
- Cross-border cooperation hotline: Contact the Interpol regional office, and the clues will be shared with the joint manhunt teams of the U.S., Canada, and Mexico.
- The FBI emphasizes that all reporting information will be kept strictly confidential, and those providing clues do not need to disclose their identity to claim the reward.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




