Original Author: GoPlus Security Team
Abstract
GoPlus Security Module (GSM) can be natively integrated into customized BNB Chain node clients.
In the replication test of 100 real attack transactions, GSM successfully intercepted 97—detection rate 97%.
In the past year, it has prevented over $22 million in user asset losses.
After integration, the delay for a single transaction increases by 40ms, with zero crashes under 1000 TPS pressure.
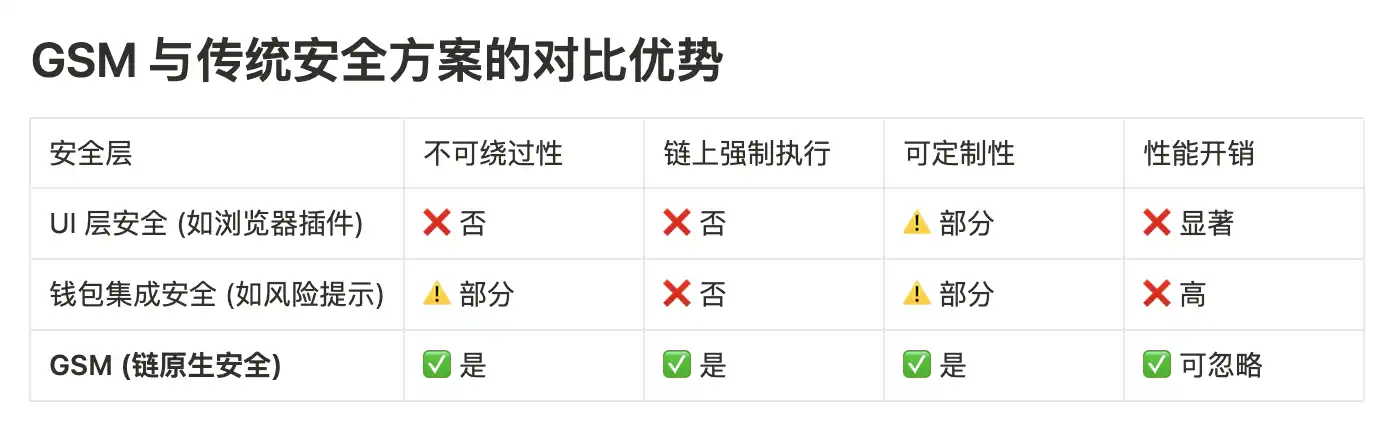
Unlike wallet or API solutions, GSM cannot be bypassed, intercepting transactions before they enter the memory pool.
GSM: A Security Firewall on the Blockchain Client Side
GSM is a lightweight modular SDK or API service that can be embedded in wallets, dApps, RPC services, Layer 2 sequencers, and full nodes. Its core is to establish a bridge between user transactions and the GoPlus security service network:
- When a transaction is triggered, GSM captures the transaction data and sends it to the GoPlus security network;
- GoPlus analyzes risks in real-time using AI algorithms (including transaction data and user security policies);
- Returns security assessment results, and GSM executes release or interception actions.
Unlike traditional Web2 security solutions, GSM is built directly on the blockchain layer, forming a secure isolation boundary between on-chain and off-chain environments. This architecture:
· Eliminates reliance on external Web2 facilities;
· Addresses the weakest links in traditional security;
· Even if the Web2 layer UI/UX is compromised, user assets remain protected.
This test was directly integrated into the BNB Chain node.
GSM's Dual-Stage Transaction Filtering Mechanism
1️⃣ Pre-Memory Pool Transaction Screening (Sentinel Defense)
When a transaction is submitted via RPC calls like eth_sendRawTransaction, GSM scans instantly before entering the memory pool:
· Target: Intercept clearly malicious transactions (e.g., blacklisted addresses, known malicious contract interactions)
· Advantage: Prevents harmful transactions from spreading, reduces memory usage, and saves node resources.
2️⃣ Pre-Packaged Context Batch Analysis
Triggered before a transaction transitions from queued state to pending state:
· Target: Conduct context-aware deep analysis of transaction sequences (grouped and sorted by from address and nonce).
· Capability:
Detect complex vulnerabilities such as multi-step reentrancy attacks;
Identify fraudulent sequences across multiple transactions (e.g., withdrawing after false liquidity injection);
Assess batch transaction risks through cumulative risk scoring (which cannot be achieved through single transaction analysis).
Intelligent Cache Layer
Stores recent scan results to avoid repeated analysis of high-frequency benign activities—ensuring high throughput and low latency.
Open Source Address
The modified BNBChain node client and test data have been open-sourced, available here.
Risk Detection Model: 12+ Dimensional Features
GSM evaluates transactions through a multi-factor weighted scoring model:
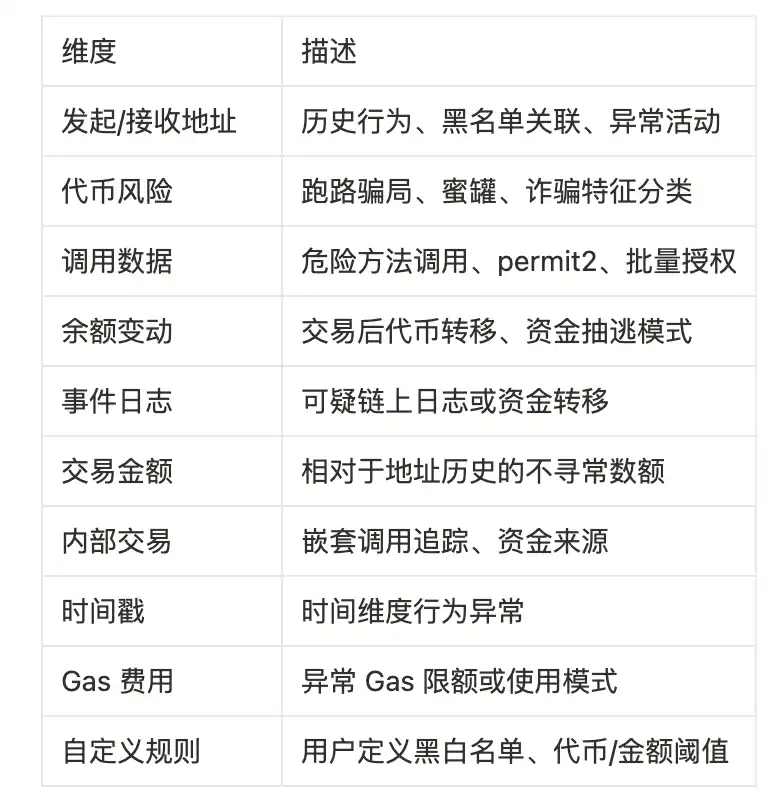
Outputs risk scores (0–100) and handling strategies:
· 0–20: Low risk → Release
· 21–60: Medium risk → Mark
· 61–100: High risk → Intercept (default)
Thresholds can be adjusted according to wallet, user, or node policies.
Performance Benchmark Testing: gRPC Interface
GSM provides two high-performance interfaces:
· EVMRiskScore (single transaction assessment)
· EVMBatchRiskScore (batch transaction analysis)
Testing Environment
· Network: BNBChain Chapel Testnet
· Hardware:
8-core CPU
16GB RAM
500GB NVMe SSD
· Software:
BNBChain Full Node (v1.1.18) + GSM Module
· Load Tools:
Parallel gRPC client simulator
Latency analysis performance probe
GoPlus historical attack scenario replication testing suite
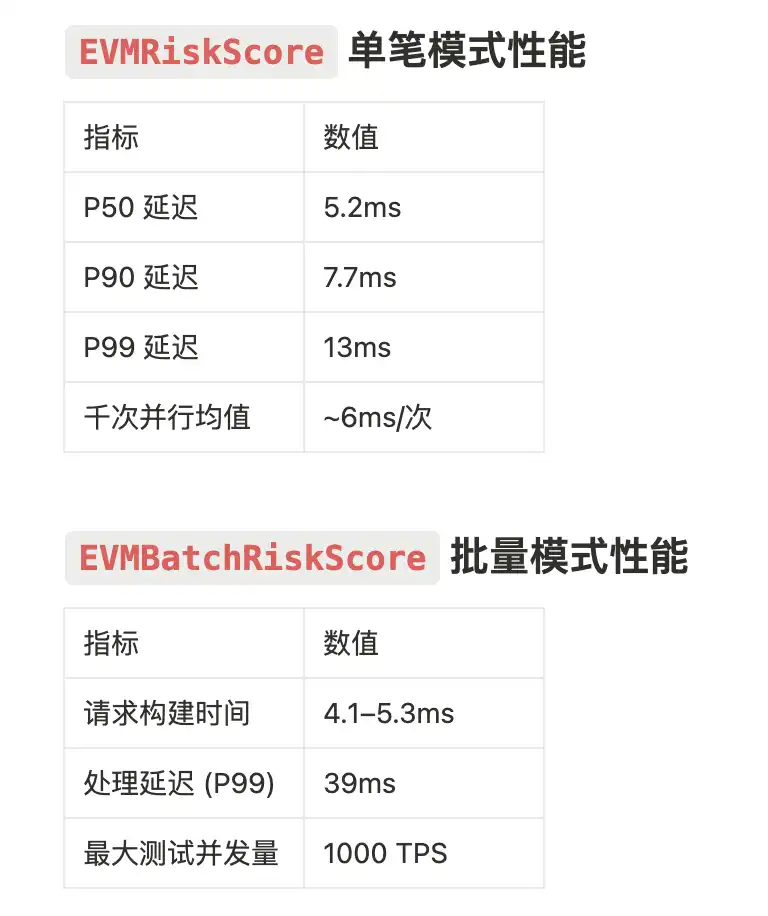
Result: With GSM enabled, the node operated stably for 24 hours under 1000 TPS load—zero crashes, zero synchronization failures.
Open Source Address
The modified BNBChain node and experimental data can be found here.
Real Attack Detection Test: 100 Exploit Transactions
Testing Method:
- Select 100 historical attack transactions from BNBChain (April 2024 – May 2025)
- Rebuild account and block states on the Chapel testnet
- Replay transactions through the GSM node
- Record GSM decisions and scores
- Data sources: ScamSniffer, CyversAlerts, and 10 other security agencies
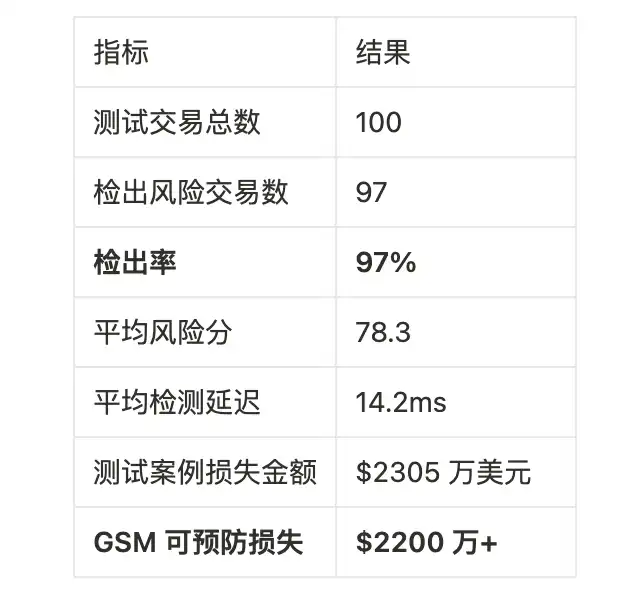
Attack Case Analysis
Case #1: Phishing Authorization Trap
· Type: Fake airdrop website + malicious "approve" authorization
· Risk Score: 100
· Features:
Phishing Score: 82
Receiving Address Risk: 82
Function Pattern: Unlimited authorization
User Behavior Anomaly: 23
→ Intercept
Case #2: Honey Pot Token (Buy Only)
· Type: Tokens that users can buy but cannot sell
· Risk Score: 100
· Features:
Exit Scam Score: 100
Receiving Address Risk: 68
Abnormal Input Amount: 24
→ Intercept
Case #3: DeFi Contract Exploit
· Type: Hacker exploits reentrancy vulnerability through underlying calls
· Risk Score: 100
· Features:
Vulnerability Pattern Match: 90
Initiating Address Marked Risk: 90
Call Data Pattern Anomaly: 82
→ Intercept
Call to Action
Security protection should not be a remedial measure. GSM proves that it is possible to intercept malicious transactions before they take effect without modifying the consensus mechanism!
We call on the following participants to deploy GSM as the default security layer:
· L1/L2 blockchain teams
· Rollup-as-a-Service (RaaS) providers
· RPC node providers
· DApp and wallet infrastructure teams
Try it now: service@gopluslabs.io; Documentation
This article is contributed and does not represent the views of BlockBeats.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




