When these 10 warning signs appear, it indicates that you may have been targeted by hackers.
Written by: Christoper Rosa
Translated by: AididiaoJP, Foresight News
Even this cybersecurity expert almost fell victim
Last weekend, reports emerged that a massive dataset containing 16 billion user identities began circulating online, which includes both previously leaked information and newly stolen login data. It is still unclear who updated this dataset and republished it. Although most of the database consists of reorganized data from past breaches, the newly updated data is concerning. This dataset is considered one of the largest collections of leaked accounts ever.
Hackers are using this data to launch various attacks, and I became one of their targets.
The phishing attack launched against my personal devices and accounts on June 19 was the most sophisticated attack I have encountered in my ten-year cybersecurity career. The attackers first created the illusion that my accounts were being attacked across multiple platforms, then impersonated Coinbase employees to offer "help." They combined classic social engineering tactics with coordinated strategies across SMS, phone calls, and forged emails, all designed to create a false sense of urgency, credibility, and scale. This false attack was widespread and highly authoritative, which is key to its deceptive nature.
The following will detail the attack process, analyze the warning signs I noticed during this process, and the protective measures I took. I will also share key lessons and practical advice to help cryptocurrency investors secure themselves in an increasingly threatening environment.
Historical data and newly leaked data can be used by hackers to implement highly targeted multi-channel attacks. This further underscores the importance of layered security, clear user communication mechanisms, and real-time response strategies. Both institutional and individual users can gain practical tools from this case, including verification protocols, domain recognition habits, and response steps that can help prevent a momentary lapse from turning into a significant security breach.
SIM Card Hijacking
The attack began around 3:15 PM Eastern Time on Thursday, with an anonymous text message stating that someone was attempting to trick my mobile carrier into leaking my phone number to others, a tactic known as SIM swapping.
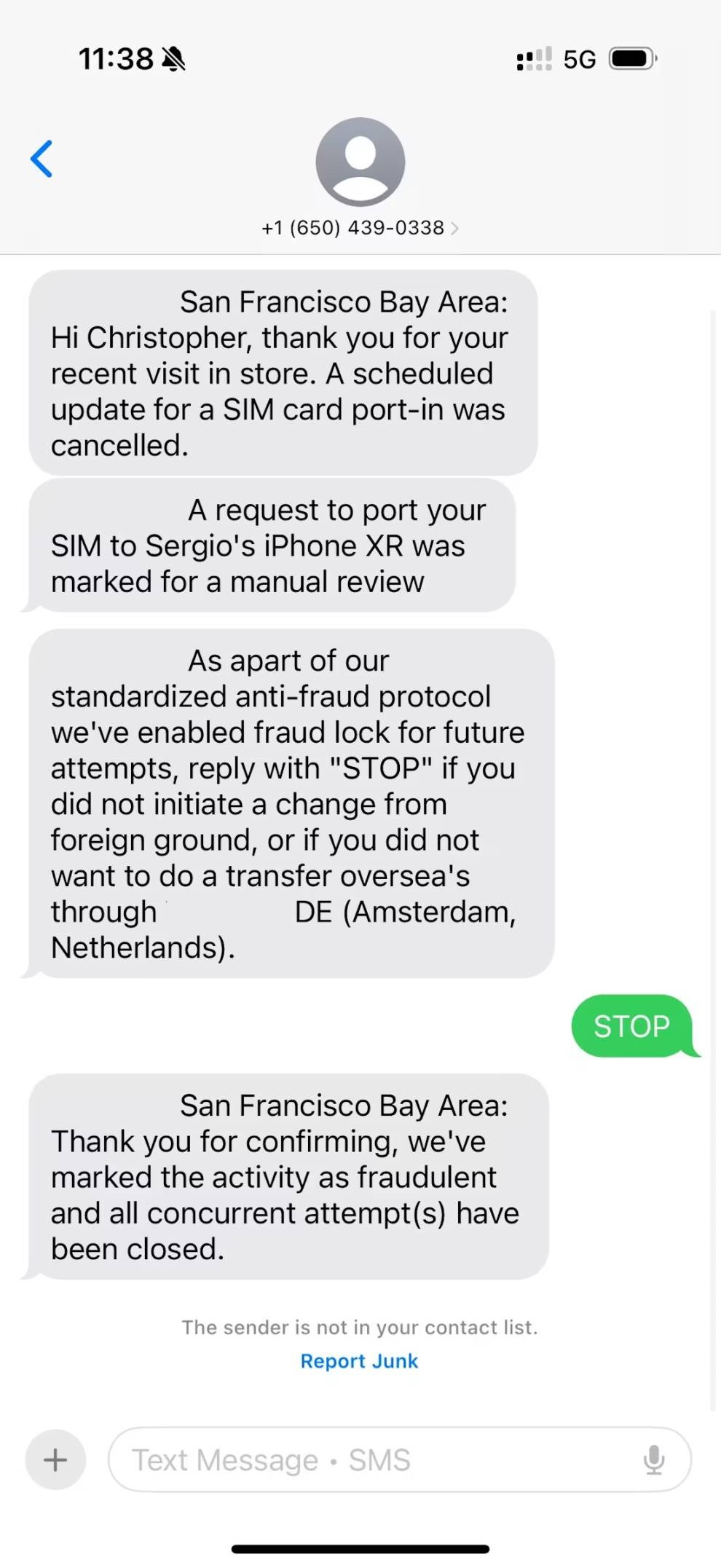
Note that this message did not come from a text number but from a regular 10-digit phone number. Legitimate businesses sending texts will use short codes. If you receive a text from an unknown standard-length number claiming to be a business, it is likely a scam or phishing attempt.
The messages also contained contradictory information. The first text indicated the leak was from the San Francisco Bay Area, while subsequent messages claimed it occurred in Amsterdam.
If SIM swapping is successful, it can be extremely dangerous because the attacker can obtain the one-time verification codes that most companies use to reset passwords or access accounts. However, this was not a real SIM swap; the hackers were laying the groundwork for a more sophisticated scam.
One-Time Verification Codes and Password Resets
The attack then escalated, and I began receiving one-time verification codes supposedly from Venmo and PayPal, sent via SMS and WhatsApp. This led me to believe that someone was trying to log into my accounts on various financial platforms. Unlike the suspicious carrier texts, these verification codes indeed came from seemingly legitimate short codes.
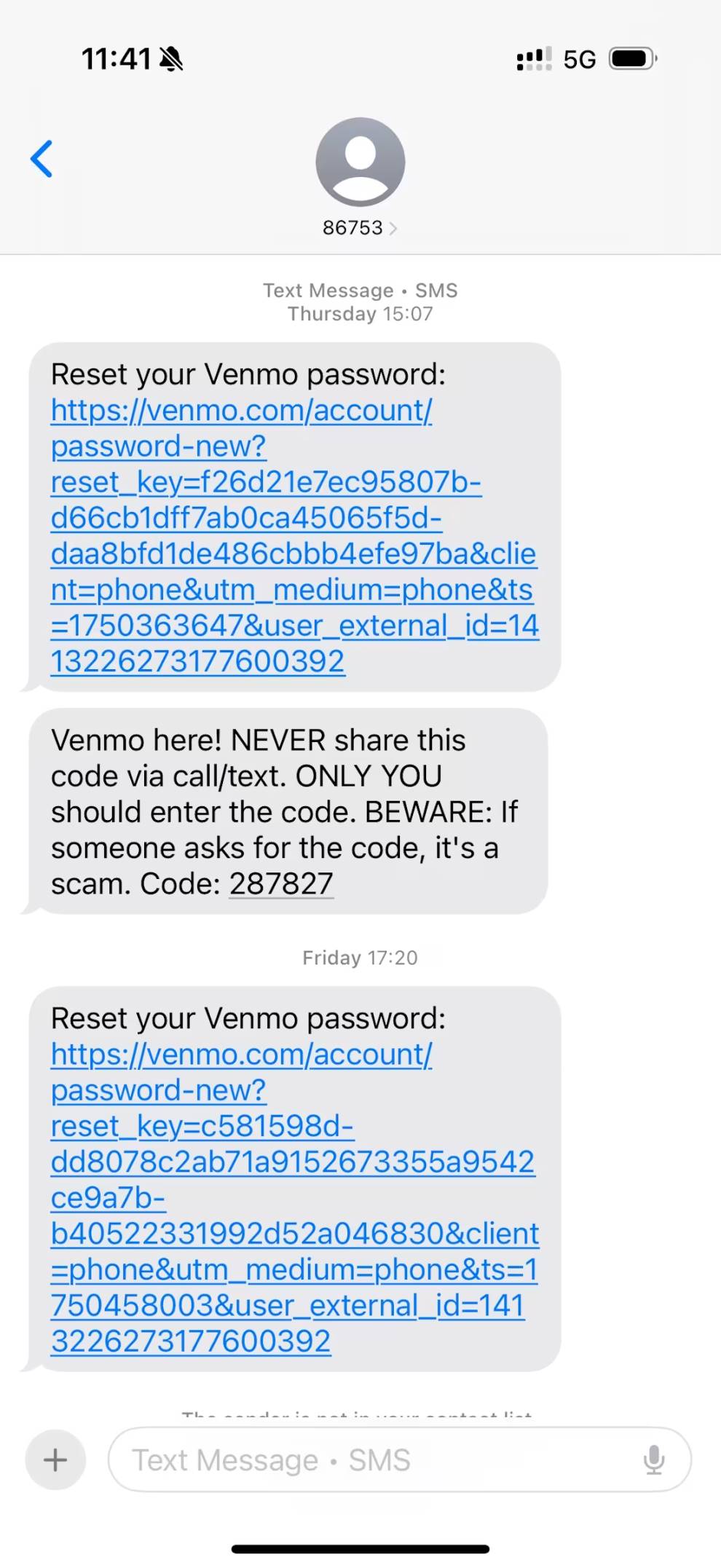
Coinbase Phishing Call
About five minutes after receiving the texts, I received a call from a California number. The caller, claiming to be "Mason," spoke with a genuine American accent and said he was from the Coinbase investigation team. He stated that there had been over 30 attempts to reset passwords and hack accounts through the Coinbase chat window in the past 30 minutes. According to "Mason," the so-called attacker had passed the first layer of security verification for password resets but failed at the second layer.
He told me that the attacker could provide the last four digits of my ID, my full driver's license number, my home address, and my full name, but failed to provide my complete ID number or the last four digits of the bank card associated with my Coinbase account. Mason explained that this contradiction triggered an alert from the Coinbase security team, prompting them to contact me to verify the authenticity.
Legitimate exchanges like Coinbase would never proactively call users unless you initiated a service request through their official website. To learn more about exchange customer service protocols, please read this Coinbase document.
Security Check
After delivering this "bad news," Mason suggested protecting my account by blocking additional attack channels. He started with API connections and associated wallets, claiming he would revoke their access to reduce risk. He listed several connected entities, including Bitstamp, TradingView, and MetaMask wallets, some of which I did not recognize, but I assumed I might have set them up and forgotten.
At this point, my guard was down, and I even felt reassured by Coinbase's "proactive protection."
Up to this point, Mason had not asked for any personal information, wallet addresses, two-factor verification codes, or one-time passwords, which are typically common requests from phishers. The entire interaction felt very secure and preventive.
Subtle Pressure Tactics
Next came the first attempt to apply pressure by creating a sense of urgency and vulnerability. After completing the so-called "security check," Mason claimed that my account had been marked as high risk, and the account protection of the Coinbase One subscription had been terminated. This meant that my Coinbase wallet assets were no longer covered by FDIC insurance, and if the attacker successfully stole funds, I would not be able to receive any compensation.
Looking back, this line of reasoning should have raised obvious red flags. Unlike bank deposits, cryptocurrency assets are never protected by FDIC insurance. While Coinbase may store customer dollars in FDIC-insured banks, the exchange itself is not an insured institution.
Mason also warned that a 24-hour countdown had begun, and overdue accounts would be locked. Unlocking would require a complex and lengthy process. More frighteningly, he claimed that if the attacker obtained my full Social Security number during this time, they could even steal funds while the account was frozen.
Later, I consulted the real Coinbase customer service team and learned that locking accounts is indeed a recommended security measure. The unlocking process is actually simple and secure: provide a photo of your ID and a selfie, and the exchange can quickly restore access after verifying your identity.
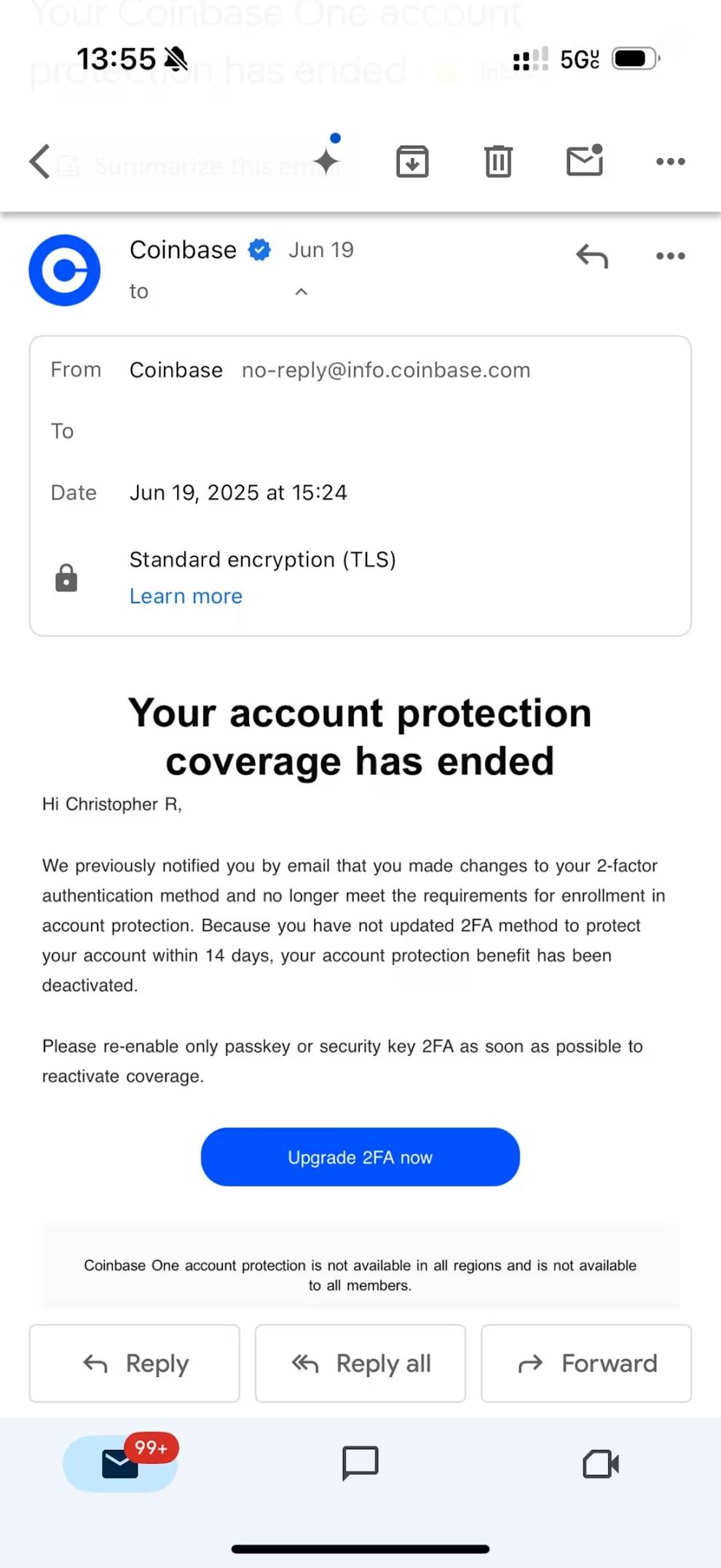
I then received two emails. The first was a confirmation of my subscription to Coinbase Bytes news, which was just a normal email triggered by the attacker submitting my email through the official website form. This was clearly an attempt to confuse my judgment by using official Coinbase emails to enhance the credibility of the scam.
The second, more disturbing email came from no-reply@info.coinbase.com, stating that my Coinbase One account protection had been canceled. This email, seemingly from a legitimate Coinbase domain, was highly misleading—if it had come from a suspicious domain, it could have been easily recognized, but because it appeared to be from an official address, it seemed authentic.
Suggested Remedial Measures
Mason then suggested transferring my assets to a multi-signature wallet called Coinbase Vault to ensure security. He even encouraged me to Google "Coinbase Vault" to review the official documentation to prove that this was a legitimate service from Coinbase over the years.
I expressed my unwillingness to make such a significant change without thorough investigation. He expressed understanding and encouraged me to research carefully while supporting me in contacting my carrier to prevent SIM swapping. He said he would call back in 30 minutes to continue the next steps. After hanging up, I immediately received a text confirming the call and the appointment.
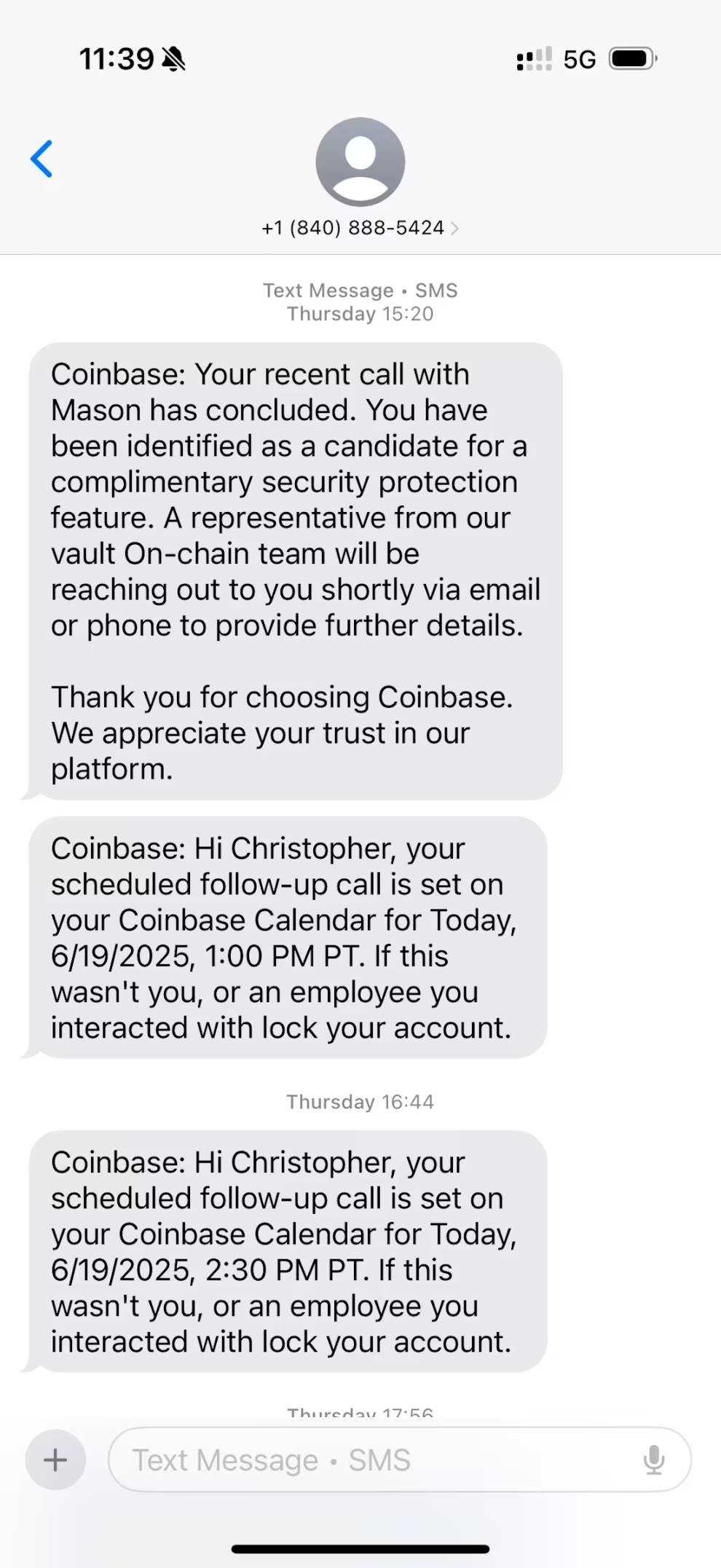
Callback and Coinbase Vault
After confirming with my carrier that there were no SIM transfer attempts, I immediately changed all my account passwords. Mason called back as promised, and we began discussing the next steps.
At this point, I had verified that Coinbase Vault is indeed a legitimate service provided by Coinbase, which is a custodial solution that enhances security through multi-signature authorization and a 24-hour withdrawal delay, but it is not a true self-custody cold wallet.
Mason then sent a link to vault-coinbase.com, claiming it could review the security settings discussed in the initial call. After completing the review, I could transfer assets to the Vault, and at that moment, my cybersecurity expertise finally kicked in.
After entering the case number he provided, the page that opened displayed the so-called "removed API connections" and a "Create Coinbase Vault" button. I immediately checked the website's SSL certificate and found that this newly registered domain, just a month old, had no connection to Coinbase. While SSL certificates can often create an illusion of legitimacy, legitimate business certificates have clear ownership, and this discovery made me stop all operations immediately.
Coinbase clearly states that it will never use unofficial domains. Even when using third-party services, it should be subdomains like vault.coinbase.com. Any operations involving exchange accounts should be conducted through the official app or website.
I expressed my concerns to Mason, emphasizing that I only wanted to operate through the official app. He argued that using the app would result in a 48-hour delay, while the account would be locked after 24 hours. I again refused to make a hasty decision, and he then stated that he would escalate the case to the "Level 3 support team" in an attempt to restore my Coinbase One protection.
After hanging up, I continued to verify the security of other accounts, and my sense of unease grew stronger.
Level 3 Support Team Call
About half an hour later, I received a call from a Texas number. Another American-accented individual claimed to be a Level 3 investigator handling my Coinbase One recovery request. He stated that a 7-day review period was required, during which the account would remain uninsured. He also "kindly" suggested opening multiple Vaults for different on-chain assets, appearing professional but never mentioning specific assets, only vaguely referring to "Ethereum, Bitcoin, etc."
He mentioned that he would apply to the legal department to send chat records and then began promoting Coinbase Vault. As an alternative, he recommended a third-party wallet called SafePal. While SafePal is indeed a legitimate hardware wallet, this was clearly a setup to gain trust.
When I questioned the vault-coinbase.com domain again, he still tried to dispel my doubts. At this point, the attacker likely realized that success was unlikely and ultimately abandoned this phishing attempt.
Contacting Real Coinbase Customer Service
After ending the call with the second fake customer service representative, I immediately submitted a request through Coinbase.com. A real customer service representative quickly confirmed that there were no unusual logins or password reset requests on my account.
He suggested locking the account immediately and collecting details of the attack to submit to the investigation team. I provided all fraudulent domain names, phone numbers, and attack methods, specifically inquiring about the sender permissions of no-reply@info.coinbase.com. The customer service representative acknowledged that this was very serious and promised that the security team would conduct a thorough investigation.
When contacting exchange or custodian customer service, always do so through official channels. Legitimate businesses will never proactively contact users.
Experience Summary
Although I was fortunate not to be scammed, as a former cybersecurity professional, this near-miss experience left me deeply unsettled. Had it not been for my professional training, I might have fallen victim. If it had been just a regular unknown call, I would have hung up immediately. It was the attackers' meticulously designed series of actions that created a sense of urgency and authority, making this phishing attempt so dangerous.
I have summarized the following warning signs and protective advice, hoping to help cryptocurrency investors secure their funds in the current online environment.
Warning Signs
Coordinated False Alerts Creating Confusion and Urgency
The attackers first created the illusion of simultaneous attacks across multiple platforms through a series of SIM card swap alerts and one-time verification code requests from services like Venmo and PayPal (sent via both SMS and WhatsApp). This information likely only required obtaining my phone number and email, which are easily accessible. At this stage, I believed the attackers had not yet obtained deeper account data.
Mixing Short Codes with Regular Phone Numbers
The phishing messages were sent using a combination of SMS short codes and regular phone numbers. While businesses typically use short codes for official communications, attackers can spoof or recycle these short codes. However, it is important to note that legitimate services will never use regular phone numbers to send security alerts. Messages from standard-length numbers should always be treated with suspicion.
Requests to Operate via Unofficial or Unfamiliar Domains
The attackers asked me to visit a phishing site hosted on vault-coinbase.com, which at first glance seemed normal but was actually unrelated to Coinbase. Before entering any information, always carefully check the domain name and SSL certificate. Operations involving sensitive accounts should only be conducted on the company's official domain or application.
Unsolicited Calls and Follow-Up Communications
Coinbase and most other financial institutions will never call you unless you have initiated a support request. Receiving a call claiming to be from a "Level 3 investigation team" is a significant warning sign, especially when such calls coincide with intimidation tactics and complex account protection explanations.
Unsolicited Emergency Situations and Consequence Warnings
Phishing attackers often exploit fear and urgency to force victims into taking action without thinking. In this case, threats regarding account locking, asset theft, and cancellation of insurance coverage are typical social engineering tactics.
Requests to Bypass Official Channels
Any suggestion to avoid using the company's official application or website, especially when these suggestions claim to provide "faster" or "safer" alternatives, should immediately raise red flags. Attackers may provide seemingly legitimate links that actually point to malicious domains.
Unverified Case Numbers or Support Tickets
Providing a "case number" to introduce a custom-built phishing portal creates an illusion of legitimacy. No legitimate service would require users to verify their identity or perform actions through an external custom link with a case number.
Mixing True and False Information
Attackers often mix real personal information (such as email or partial Social Security numbers) with vague or inaccurate information to enhance credibility. Any inconsistencies or vague references to "chains," "wallets," or "security checks" should raise suspicion.
Using Real Company Names in Alternative Suggestions
Introducing trusted names like SafePal (even if these companies are indeed legitimate) may be a strategy to divert attention. This practice provides the appearance of choice and legitimacy while actually guiding victims toward malicious actions.
Excessive Enthusiasm Without Verification
Attackers may appear very patient, encouraging me to do my own research, and initially not asking for sensitive information. This behavior mimics that of real customer service personnel, making the scam seem professional. Any unsolicited help that seems "too good to be true" should raise suspicion.
Proactive Protective Measures and Recommendations
Enable Transaction-Level Verification on Exchanges
Enable two-factor authentication and verification based on codes in the exchange settings. This ensures that any attempts to send or transfer funds require real-time confirmation sent to your trusted device, preventing unauthorized transactions.
Always Contact Service Providers Through Legitimate, Verified Channels
In this case, I contacted my mobile service provider and Coinbase by directly logging into the official platforms and submitting support requests. This is the safest and only appropriate way to interact with customer service when account security is threatened.
Exchange Customer Service Representatives Will Never Ask You to Move, Access, or Protect Funds
They will also not ask for or provide your wallet recovery phrases, will not request your two-factor verification codes, and will not attempt to remotely access or install software on your device.
Consider Using Multi-Signature Wallets or Cold Wallet Storage Solutions
Multi-signature wallets require multiple approvals to authorize transactions, while cold wallets keep your private keys completely offline. Both methods effectively protect long-term held assets from remote phishing or malware attacks.
Bookmark Official URLs and Avoid Clicking Links from Unsolicited Information
Manually entering URLs or using trusted bookmarks is the best way to avoid domain spoofing.
Use Password Managers to Identify Suspicious Websites and Maintain Strong Passwords
Password managers help prevent phishing attempts by refusing to auto-fill on fake or unknown domains. Regularly change passwords, and if you suspect malicious attacks, change your passwords immediately.
Regularly Review Associated Applications, API Keys, and Third-Party Integrations
Revoke access for any applications or services you no longer use or cannot identify.
Enable Real-Time Account Alerts Where Available
Notifications for logins, withdrawals, or security setting changes can provide critical early warnings of unauthorized activity.
Report All Suspicious Activity to the Official Support Team of the Service Provider
Early reporting helps prevent broader attacks and contributes to the overall security of the platform.
Conclusion
For financial institutions, IT security teams, and executives, this attack highlights how historical data can be repurposed and combined with real-time social engineering to bypass even the most mature security defenses. Threat actors no longer rely solely on brute force attacks but execute coordinated cross-channel strategies to gain trust and deceive users by mimicking legitimate workflows.
We must not only protect systems and network security but also recognize threats and take action to protect ourselves. Whether working at a cryptocurrency institution or managing crypto assets at home, everyone must understand how personal security vulnerabilities can evolve into systemic risks.
To guard against these threats, institutions must implement layered defenses, such as domain monitoring, adaptive authentication, anti-phishing multi-factor authentication, and clear communication protocols. Equally important is that companies cultivate a culture of cybersecurity awareness, ensuring that every employee, from engineers to executives, understands their role in protecting the enterprise. In today's environment, security is not just a technical function but a responsibility that must be shared from individuals to the entire organization.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




