The Binance risk control team, in collaboration with academia, has proposed a new detection system based on "AI + blockchain graph analysis" to identify witch addresses.
Written by: Nicky, Foresight News
This article is compiled based on the paper "Detecting Sybil Addresses in Blockchain Airdrops: A Subgraph-based Feature Propagation and Fusion Approach."
Recently, Binance's risk control department, together with Zand AI and ZEROBASE, published a paper on witch attacks. To help readers quickly understand the core content of the paper, the author has summarized the following key points after studying the paper.
In cryptocurrency airdrop activities, there is always a group of special players operating in the shadows. They are not ordinary users but utilize automated scripts to create hundreds or even thousands of fake addresses—these are the infamous "witch addresses." These addresses cling to well-known projects' airdrop activities like parasites, such as Starknet and LayerZero. They erode the project's budget, dilute rewards for real users, and undermine the foundation of blockchain fairness.
In the face of this ongoing technical cat-and-mouse game, the Binance risk control team, in collaboration with academic institutions, developed an AI detection system called "Subgraph-based lightGBM," achieving an accuracy rate of 90% in real data tests.
Three "IDs" of Witch Addresses
Why can these cheating addresses be accurately identified? The research team analyzed the transaction records of 193,701 real addresses (of which 23,240 were confirmed as witch addresses) and found that they inevitably leave behind three types of behavioral traces:
Temporal fingerprints are the primary giveaway. The operations of witch addresses exhibit a bizarre "precise timing" characteristic: from the first receipt of gas fees, completing the first transaction, to participating in airdrop activities, these key steps are usually completed in a very short time frame. In contrast, the operation time distribution of real users is random; after all, no one would create an address just to claim an airdrop and then immediately discard it.
Financial trajectories reveal economic motives. The balances of these addresses always remain at a "just enough" state: slightly above the minimum amount required for airdrop eligibility (to save on costs), and once they receive rewards, they quickly transfer them out. More notably, when they operate in bulk, the transfer amounts show a high degree of consistency, unlike real user transactions, which exhibit natural fluctuations.
Relational networks serve as ultimate evidence. By constructing transaction graphs, the team observed three typical topological structures:
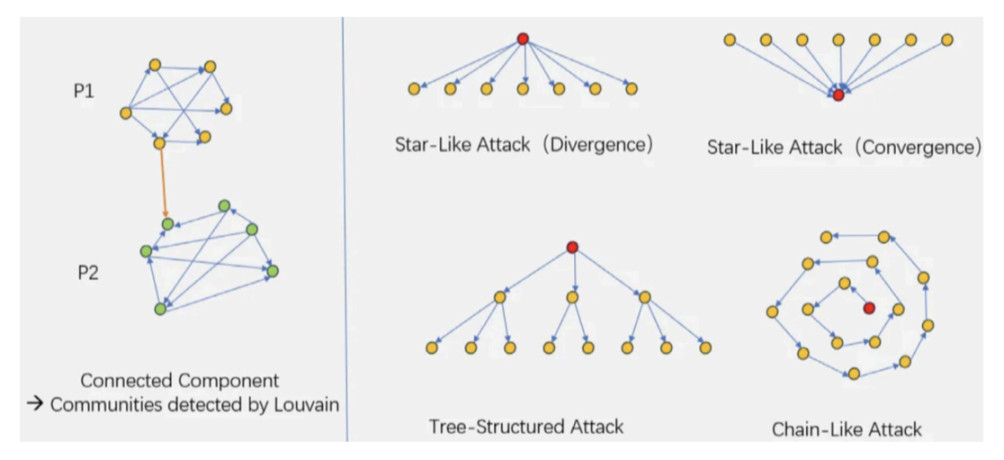
Star network: A "command center" distributes funds to dozens of sub-addresses.
Chain structure: Funds are linearly passed between addresses like a relay baton to create false active records.
Tree diffusion: Attempts to evade detection using a multi-layer branching structure.
These patterns expose the coordinated nature of programmatic operations, which is also the most challenging feature for traditional detection methods to replicate.
Two-layer Relationship Network: The Detective's Tool
Tracking transaction data across the entire blockchain is like finding a needle in a haystack. The research team adopted a two-layer transaction subgraph model—similar to a detective investigation, where not only the target individual (address A) is examined, but also their direct contacts (addresses that transferred to A, addresses A has transferred to) and the associates of these contacts (secondary relationships).
More importantly, the innovative "feature fusion technology": the system aggregates the behavioral features of neighboring addresses into a "behavior profile" for the target address. For example, it calculates the minimum, maximum, average, and fluctuation of the amounts transferred out by all associated addresses, forming composite indicators that describe the patterns of fund flow; or it assesses the in-degree and out-degree (number of associated addresses) of neighbors to determine network density. This design allows the system to maintain efficiency while analyzing over 5.8 million transactions, avoiding the computational disaster of traditional methods that track data across the entire network.
Practical Testing: Capturing "Ghosts" in Binance Airdrops
This system was tested against real airdrop data from Binance's Soulbound Token (BAB). BAB is a soulbound token launched by Binance in 2022 to verify the identities of real users who have completed KYC, making it an ideal testing ground for detecting witch behavior.
The team first manually analyzed and clustered to filter out suspicious addresses, establishing an appeal review mechanism to confirm the final witch address labels. During data cleaning, institutional addresses (such as exchange hot wallets), smart contracts, and addresses that have been active for over a year (witches often discard old addresses to avoid detection) were excluded to ensure the purity of the dataset.
The results showed that the new method achieved high accuracy in identifying three types of cheating networks:
Star network identification rate of 99% (previous method's maximum 95%)
Chain structure identification rate of 100% (previous method's maximum 95%)
Tree diffusion identification rate of 97% (previous method's maximum 95%)
All four core metrics surpassed 0.9: precision reached 0.943 (previous optimal model was 0.796), recall rate reached 0.918 (meaning over 91% of witch addresses were captured), F1 score reached 0.930, and AUC value reached 0.981 (close to perfect classification). This means that project teams can significantly reduce the risk of mistakenly targeting real users while closing loopholes for cheating.
Technical Boundaries and Future Battlefields
This technology is currently mainly applicable to long-term airdrop scenarios (such as phased distribution of soulbound tokens), as these activities can accumulate enough labeled data for AI learning. In terms of blockchain compatibility, it supports Ethereum Virtual Machine (EVM) compatible chains (such as BNB Chain, Polygon) but is not yet applicable to UTXO model chains like Bitcoin. However, the paper notes that high gas costs make airdrop activities rarely conducted on UTXO chains, so the actual impact is limited.
The research team emphasizes that the potential of this technology extends far beyond the airdrop field. Since it identifies anomalies through transaction networks and behavioral patterns, it can also be applied to:
Detect market manipulation behaviors (such as coordinated addresses in pump and dump schemes).
Assess token liquidity risks (identifying fake trading pairs).
Build on-chain credit scoring systems.
As witch attack strategies continue to evolve, this technological arms race to protect the fairness of Web3 will drive detection systems to iterate towards smarter and more universal solutions.
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




