原文来源:OKX
2025 年,Web3 进入「更大规模、更高频使用」的新阶段,钱包也随之从「存币工具」加速演进为链上入口与交易操作系统。市场研究机构 Fortune Business Insights 预计,加密钱包市场 2025 年规模约为 122 亿美元,并可能在 2034 年增长至 985.7 亿美元。
用户侧的扩张同样明显:a16z crypto 在《State of Crypto 2025》中估算,活跃加密用户约 4000–7000 万,而「持币但不一定链上活跃」的加密资产持有者约为 7.16 亿;Crypto.com Research 的报告也给出 2025 年上半年全球加密持有者由 6.81 亿增至 7.08 亿的口径。
规模与渗透率上升的另一面,是安全风险被同步放大。它不再只是「合约有没有漏洞」,而是能否在用户的关键节点,比如点击链接、连接钱包、签名授权、转账收款等节点,提前把风险拦住。
链上世界的「攻击面」往往不止于合约漏洞,更常见于低门槛的钓鱼、假域名、冒充客服、授权欺诈等「交易前风险」。例如 Chainalysis 对「crypto drainers(钱包清空器/钓鱼授权工具)」的定义就指出,这类工具并非盗取账号密码,而是诱导用户连接钱包并批准恶意交易授权,从而直接转走资产。公开数据也显示,2024 年「钱包清空器」相关损失接近 5 亿美元量级。
因此,提升 Web3 钱包的安全将不再只关注于合约是否有漏洞,而需要进一步关注如何在用户行为的关键节点提前进行风险拦截,即「交易前安全」
在这样的行业背景下,「安全」越来越难以用一句口号解决,反而更像是一套需要被持续证明的治理能力:能否被验证、能否被追溯、能否及时披露,正在成为用户选择钱包的重要依据。
从「安全宣称」到「可理解的安全能力清单」
过去很长一段时间里,钱包项目谈安全,常见话术是「我们做过审计」「我们有白皮书」「我们很重视风控」。但随着诈骗与钓鱼的产业化,这种「安全宣称」正在失去说服力。用户真正出事的瞬间,往往发生在点击链接、连接钱包、签名授权这些极短的交互里。Chainalysis 形容的「crypto drainers(钱包清空器)」就是典型路径:攻击者伪装成合法页面,引导用户完成授权,资产随即被转走;其研究中甚至提到伪造 Magic Eden 页面、面向 Ordinals 用户实施恶意交易的案例。
公开数据也在推动行业叙事转向「可理解」。Security Week 援引 Scam Sniffer 的统计称,2024 年通过钱包清空器造成的盗损接近 5 亿美元,受害者超过 33.2 万——这类事件并不要求攻击者突破复杂系统,更多依赖用户在交互时「看不懂风险」。另一边,Chainalysis 也在 2025 年的披露中估算,2024 年链上诈骗收入至少 99 亿美元,且可能随着更多地址被识别而上修。当风险主要来自「用户侧的可读性缺口」,钱包厂商就必须把安全从后台工程,搬到前台表达。
于是,行业里越来越多的钱包开始把安全能力「产品化」:不再只告诉你「我们安全」,而是把保护动作拆成用户能理解的清单——哪些代币会被标记为高风险、哪些交易会触发预警、哪些地址或 DApp 会被拦截、为什么拦截。这种变化的本质是把安全从「资质叙事」改写成「交互叙事」:让用户在签名前就获得可执行的信息,而不是事后再去看一份审计 PDF。
在这一趋势下,OKX 钱包新上线并升级的安全中心页面,给出了一个较典型的「清单化表达」样本。其页面把面向用户的安全能力明确写成三道「前线防线」:Token risk detection、Transaction monitoring、Address screening,并分别用一句话解释其作用,比如「标记高风险代币以降低接触蜜罐和恶意方」「跨链实时监控识别可疑链上活动」「拦截与恶意 DApp 和地址的交互」。这种写法的好处在于:即便用户不懂安全术语,也能快速对应到自己正在做的动作——我现在要不要点、要不要签、要不要转。
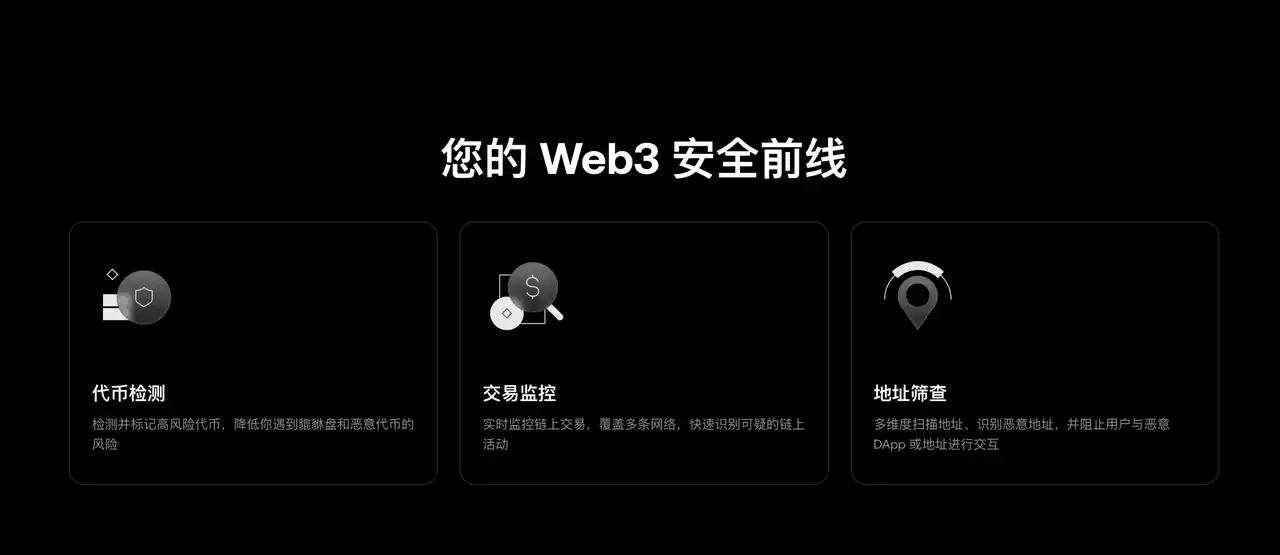
点击直达:OKX 钱包安全落地页审计报告
更重要的是,「可理解」并不等于「自说自话」。在同一页面里,OKX 钱包同时放出「View audit reports(查看审计报告)」入口,把「能力清单」与「第三方核验」连在一起。而其帮助中心的审计报告合集页则进一步把审计范围、发现问题数量与修复状态写明,让用户在需要时能从「看懂能力」走向「核验证据」。
这类「从安全宣称到可理解清单」的转变,核心价值不在于把安全说得更宏大,而在于把安全说得更可执行:当诈骗越来越依赖诱导与伪装,钱包能否把风险提示做在交互点、用用户听得懂的语言讲清楚「哪里危险、为什么危险、你该怎么做」,正在成为安全能力的一部分,并且越来越决定用户会不会在关键一步踩坑。
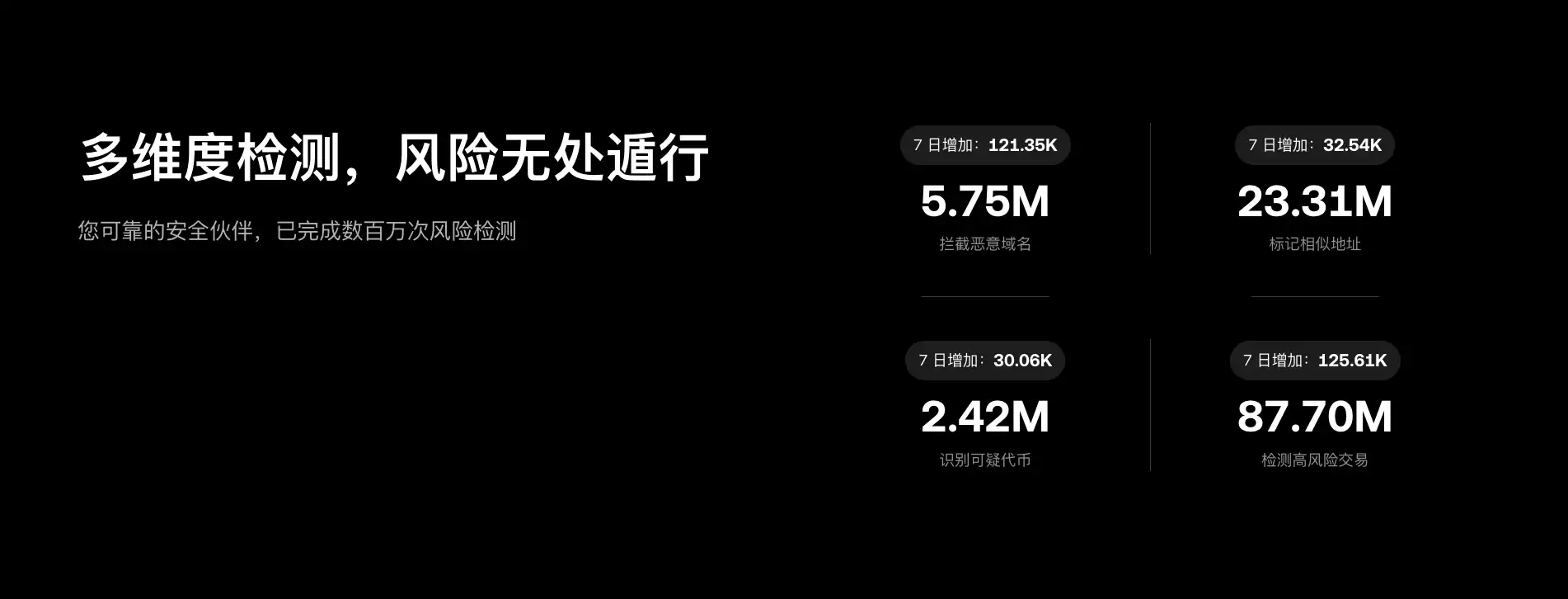
审计信息「公开可查」:把第三方背书从「有链接」变成「可复核的证据链」
在钱包行业里,审计长期存在一个现实问题:很多项目确实「做了审计」,但信息分散在公告、PDF、社媒转发里,普通用户很难快速搞清楚「谁审了、审了什么、有没有修、什么时候更新」。OKX 钱包这次更显眼的动作,是把可公开的第三方审计报告集中到统一入口,并在页面上直接标注「发布于 2022 年 11 月 11 日、更新于 2025 年 11 月 17 日」,让用户一眼就能判断这不是一次性陈列,而是持续维护的信息披露窗口。

从该合集页公开条目来看,其披露范围并未停留在「智能合约」这一传统审计对象。以 CertiK 的 2024-05-23 条目为例,审计内容明确覆盖移动端与前端的关键代码路径:包括 iOS/Android 组件、前端 ReactJS UI 组件与与 keyring 交互的 JS 控制器,以及多个钱包 SDK 模块,同时给出了审计方法和结论口径。
同一页面中,SlowMist 的条目则更贴近近两年钱包演进的「新范式」——AA 智能合约账户、MPC 无私钥钱包、Ordinals 交易模块等均被列为可公开审计对象;此外还单列「私钥安全模块」的审计信息,直接写明「私钥或助记词只存于用户设备中、不会向外部服务器发送」,用更明确的边界描述回应用户对密钥安全的核心关切。
这种「集中化展示」的价值不止是信息更齐全,更关键在于它把「新能力」与「可验证性」绑定在同一个入口:当钱包行业越来越走向 AA、MPC 等复杂架构时,用户最需要的不是一句「我们很安全」,而是能快速复核的证据——审计范围是否覆盖到关键模块、方法是什么、风险有没有闭环修复、信息是否持续更新。
同时,据 OKX 钱包介绍,本次升级后,新增审计报告与相关信息可通过配置直接更新、无需发版。如果这一机制能长期稳定运行,它实际缩短的是「对外可验证」的路径,而不仅仅是节省研发与发布成本。
对于用户而言,则意味着当审计新增或修复完成时,公开入口可以更快反映「最新状态」,减少在关键风险窗口里「只能靠转发截图/旧链接判断」的不确定性;对于第三方观察者与研究者而言,则更容易形成可追溯的时间线:哪些模块在什么时候完成审计、发现了什么级别的问题、何时确认修复并公开更新,从而把「第三方背书」真正变成持续可复核的证据链,而不是一次性陈列的 PDF。
本文来自投稿,不代表 BlockBeats 观点。
免责声明:本文章仅代表作者个人观点,不代表本平台的立场和观点。本文章仅供信息分享,不构成对任何人的任何投资建议。用户与作者之间的任何争议,与本平台无关。如网页中刊载的文章或图片涉及侵权,请提供相关的权利证明和身份证明发送邮件到support@aicoin.com,本平台相关工作人员将会进行核查。




